With the rise of cyber attacks, protecting data assets and enhancing cyber security has become a basic necessity. As the cyber threat prevention mechanisms are taking off, so is the skill set of the attackers. The techniques and methods applied for cyber attacks and exploiting vulnerabilities are getting even more sophisticated.
If you are an individual user at some, a part of an organization that handles day-to-day digital information, or an organization with sensitive digital data, it would be better to get a head start and protect all of your assets and devices from a cyber attack. This can be achieved through learning more about the types of cyber attacks so that you can think ahead and preplan the prevention and impact-reduction mitigation steps.
If you are stepping into the world of cybersecurity and want to learn the basics, this guide will tell you all about the types of cyberattacks and what they are about.
What are cyber attacks?
Before discussing its types, it is important to baby-step our way into the cybersecurity world.
A cyber attack is an unauthorized, malicious access or action carried out by a third party on a system or a network. The intention of the attack is always malicious, such as looking to harm an organization or an individual, financial gain, access to forbidden data, and such.
Unconventional methods don’t need to be used to gain access to be labeled as a “cyber attack.” Conventional methods, such as logging into an account using a username and a password, can also be considered a cyber attack if the means to obtain that confidential information is illegitimate.
Cyber attacks can be carried out by an individual or even an organization dedicated to gaining unauthorized access to information which could disrupt digital services, or provide financial gain.
Effects of a cyber attack
If you have been a victim of a cyber attack, then you could guess what the aftereffects of a cyber attack are.
Cyber attacks can have negligible effect, or be devastating, depending on the target, the type of attack, the duration of the attack, and the data/assets compromised.
For example, getting your Facebook account hacked for 2-3 minutes would not have the same effect as hacking a server with millions of financial information of millions of users.
A hacker could potentially shut down a business, temporarily or permanently, by both its digital services as well as through the organization’s reputation.
For example, flooding an organization’s servers with HTTP requests could prevent all other network traffic from communicating, causing the network traffic to a standstill. On the other hand, if the news got out that the largest digital financial data handling company has been hacked for a long time, and they are only becoming aware of it now, would make the company lose billions in shares, as well as prospective clients, as it would lose its credibility.
Amongst other effects, such as loss of revenue and legal fees, the damage to an organization’s reputation is the worst. However, if you are an individual and someone has gained unauthorized access to your computer, then the effects depend on what has been compromised. If they have created a back door to your PC, then they could access all the data and monitor your activity as they please. They may have encrypted crucial information in exchange for money, or stolen your financial record.
In the end, another major effect of a successful cyberattack is recovering from it. If not prepared, it can take days for organizations to recover from an attack and get their digital assets up and running again.
It is therefore crucial that you understand the many different types of cyberattacks, and only then will you be able to understand the remedies in practice and how they can prevent attacks, or at least, reduce the size of the impact.
Types of cyberattacks and detections
Malware
Even if you are not tech-savvy, you have heard the word “malware.” This word originated by combining the two words “malicious” and “software” – which is, in essence, the definition of malware.
Malware, often referred to as a virus or a trojan horse, is perhaps the most common kind of cyber attack. In this type of attack, a virus is placed on a system and executed behind a legitimate software, in the background. Malware can inflict different sorts of damage. While one may block your internet access, the other type can steal and transmit your personal files and folders.
There are many other types of cyber attacks discussed below that also fall into the “malware” category.
Malware is created by attackers and usually placed on the internet for the users to download, or share through legitimate-looking emails. Once the target executes the software/script, unknowingly, their device gets infected.
Now, depending on the type of malware, it can also propagate to other devices on the network, or invade itself into removable storage devices, like USBs.
Detecting malware
Malware can usually be detected after it has been executed. By that time, it was probably already too late. Apart from continuous monitoring, you can detect malware when your system starts behaving abnormally. You may start seeing ads, online redirection, uncalled pop-ups, bloatware, etc.
Other detection mechanisms involve antivirus software, firewalls, packet sniffers, etc.
Learn how to prevent malware attacks.
Ransomware
Ransomware is a form of malware, with a targeted intention. In a ransomware attack, the attacker demands a significant sum of money in exchange for leaving your device alone, not leaking your sensitive information, or decrypting everything on your hard drive which had been encrypted by the ransomware attack.
Note that in recent times, ransomware attacks have become more common, and usually, the hacker does not return a key for decrypting your data once their demands have been met.
Detecting ransomware
Like any malware, if you detect that your computer has been compromised with ransomware, it is probably too late.
If a ransomware attack has been carried out on your PC, the only way to detect is by using a tool, like antivirus software, or you’ll find that all of your files, folders, and data, have been encrypted. In this case, all icons will look the same, maybe have the same name even, and you will not be able to access them using any means.
Spyware
Another kind of malware, spyware is targeted toward fetching personal information and monitoring your activity. This information is then transmitted to the hackers.
Spyware could potentially compromise your Personal Identification Information (PII), financial credentials, passwords, emails, and pretty much everything else that you have done on your system.
Spwares are coded to avoid detection so that they can run in the background for as long as possible. Often, spyware can be seen running in the background, and when seen in the Task Manager on Windows, they can be found running with a legitimate Windows process name, to disguise themselves.
Detecting spyware
As mentioned earlier, spyware is designed to run undetected. This way, they can run longer in the background without you noticing them, and hence, can collect more information from your PC.
However, there are tools, like antiviruses, that you can use to detect and quarantine such malicious software from running in the background. A good antivirus software should immediately detect and report it to you, and isolate it without any additional input.
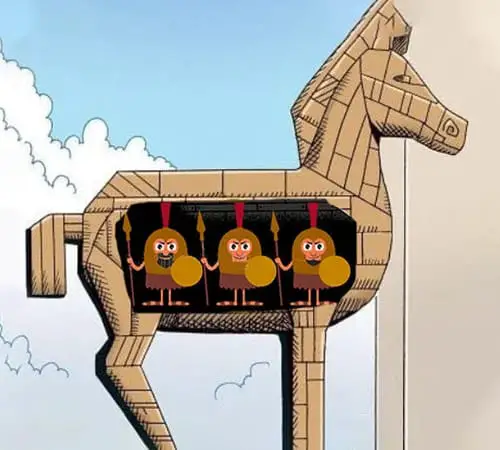
Trojans
A trojan, which refers to the “Trojan horse” that housed the ancient Greeks when conquering the city of Troy, is a kind of malware disguised as legitimate software. Or, a trojan could also piggyback and be carried on the back of legitimate software.
The true intent of a trojan virus could be many. Here are a few different types of trojan viruses:
- Backdoor trojan: A virus that seems like legitimate software to create a “backdoor” on a computer, and allows the attacker access to the machine undetected.
- Downloader trojan: Such trojans download additional malware on the target computer.
- Infostealer trojan: This kind of virus steals data from the system and communicates it to the attacker.
- Remote access trojan: This kind of trojan virus gives access, and hence the control of the PC to the attacker.
- Distributed Denial-of-Service (DDoS) trojan: Such trojans infect the device, which is then used to flood a predefined system using the device.
Any kind of malware disguised as legitimate software is considered a trojan horse.
Detecting trojan attacks
Trojans are designed to make it look like they are performing a legitimate task, while they perform other functions in the background, undetected. However, there are subtle hints that you can keep a lookout for to check whether your PC has been infected by a trojan virus. Here are a few signs:
-
Your PC is running slower than usual
Background processes like a trojan virus, when running heavy tasks, take up the system resources and slow the system’s response. If you aren’t performing any heavy tasks, and the computer still seems slower, there are chances that your PC has been infected with a virus.
-
Unwanted apps are getting installed
If you notice any apps and programs getting installed on your computer out of nowhere, the chances are, your computer is compromised.
-
Getting redirected on the web
While surfing the web, you are being redirected to malicious websites more than usual. If so, it may be possible that the trojan virus has infected your web browser.
-
You see pop-ups inside the OS
You may be seeing unwanted pop-ups with advertisements and other malicious content out of the blue. If so, this is the indication of a virus manifesting on your system.
While trojan viruses may be operating in incognito, there are signs that you can look out for and prevent your PC from havoc.
Adware
Adware displays ads, usually in pop-ups, on top of your operating system. Adware is a method for developers to generate revenue by having you interact with the ads. These are normally downloaded and executed on your computer alongside another legitimate app or software, that you probably got for free.
That said, you probably did not consent to download and execute the adware. Additionally, the adware can be annoying as it pops up without a warning, on top of other apps, and could be of any size.
Note that it is not necessary that the legitimate software be blamed for the adware. It could be possible that a third party exploited the legitimate software and injected their own adware.
Detecting adware
Most adware displays an ad inside pop-ups and dialog boxes that appear out of nowhere on your screen. However, the more sophisticated adware can subtly display ads without you noticing. Here are a few things you need to keep a lookout for in case your computer is infected with adware:
- You are seeing more ads in the web browser than usual.
- Web pages are displaying differently than usual.
- Pop-up ads even when not browsing the web.
- Slower than normal internet speeds
- Unwanted addition of toolbars and menus inside the browsers.
Cross-Site Scripting (XSS)
Cross-Site Scripting, or XSS attacks is where an attacker infects a web application or a website with a malicious piece of code. This code is then transferred onto the visitor’s browser, resulting in their devices being compromised.
The attackers usually take advantage of a vulnerability on a web page to infiltrate their own virus. For example, they can inject their codes on the download button, and when a user clicks it, instead of downloading the legitimate software, it downloads the malicious virus.
That said, there are 3 different types of XSS attacks:
- Stored (persistent) XSS: In this type of XSS attack, the malicious piece of code is saved inside the database server and transferred onto the user’s device when a data request is generated
- Reflected (non-persistent) XSS: In this case, the web app sends the virus onto the target’s web browser.
- DOM-based XSS: In this type of XSS attack, the virus is not injected into the webserver. Instead, it is reflected by client-side JavaScript code on the client-side.
Detecting XSS attacks
Detecting an XSS attack is a job for the owner of the web application or server, and not of the victim. That said, there is no simple way to detect whether the web app has been compromised. Instead, the only way is to review and analyze the code and test it for any vulnerabilities.
Additionally, you can also use tools like Vulnerability Scanner to quickly scan for vulnerabilities in your web app.
Drive-by attack
In a drive-by attack, a target only needs to visit a malicious website in order to get their device infected with malware. A drive-by attack does not require any action from the target PC, hence the term “drive-by.”
Note: In a similar attack, known as a “Drive-by download attack,” a user needs to perform an action, like clicking a Download button, in order for their device to get infected with malware.
In a drive-by attack, an insecure website is compromised by a hacker who then inserts malicious code into the website. Then, any user visiting the website will become a victim of the attack.
The severity of the impact of a drive-by attack can be different. While some attackers can open a back door to your computer, others can insert adware, spyware, or even hijack it.
Detecting drive-by attacks
If your device is infected with a drive-by attack, the symptoms will be dependent entirely on what type the attack is. For example, if it has been infected with adware, you may start seeing ads in popups. Or, you may see additional redirections while clicking on the close button on an app.
That said, there is no straightforward method for detecting whether your PC has been infected with a drive-by attack. Instead, you must look out for the symptoms of the specific type of attack.
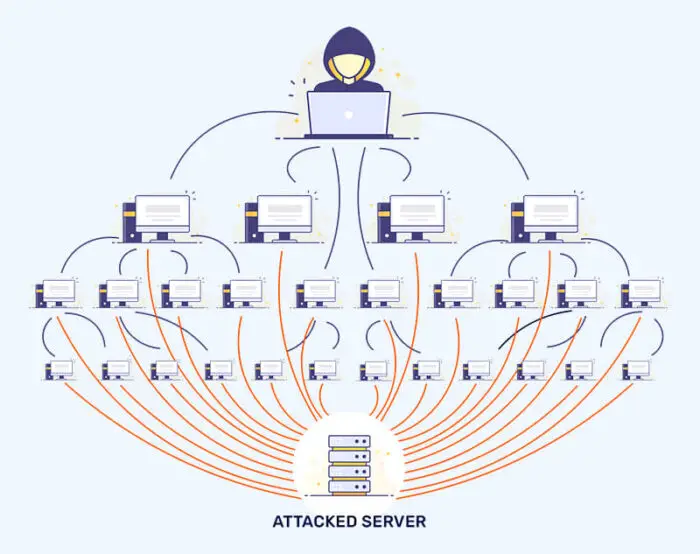
Distributed Denial of Service (DDoS)
A DoS or a DDoS attack is where a single, or multiple compromised devices are used to generate and send data packets to a single server or endpoint, making it extremely slow, or in some cases, completely incapable of performing its regular functions. This is done via bots or botnets.
The device is flooded and overwhelmed with illegitimate traffic, thus being unable to handle the actual data packets that need processing.
DDoS attacks are usually implemented to divert the attention of cybersecurity professionals from the actual attack. Since a DDoS attack benefits no one, and only disrupts a device’s or an organization’s network traffic, attackers often use an ulterior attack to obtain their objective.
When a DDoS attack is performed, certain devices need to be taken offline before the target can recover from the attack. This often leaves a vulnerability gap in the system’s security, making it a convenient target for the actual attack by hackers.
To perform a DoS or a DDoS attack, an attacker must first infiltrate a single, or many different devices and inject a malicious code without being detected. Once enough devices have been compromised, they then command those devices to attack a target host at the same time with HTTP requests, which jams or slows the entire system.
As with other attacks, DDoS attacks also have different types. Here are a few common types:
- Volumetric attacks: These are usually flood attacks where the target device or node is bombarded with so much traffic, that it exhausts itself and blocks out the genuine data packets.
- Protocol attacks: A special kind of protocol is abused in such attacks. For example, in a SYN flood attack, which is a type of protocol attack, multiple SYN requests are sent to the target device to perform a TCP handshake. The target then sends a SYN-ACK (acknowledgment) packet back to the originating IP address, for which it should then send a response again. However, the spoofed IP address never responds, and the target device crashes after waiting for the reply.
- Application layer attacks: The target device generates a response to an incoming client request, and the bot requests for the same information over and over, overwhelming the target device.
Apart from these 3 types of DDoS attacks, there are also other subtypes part of these attacks.
Detecting DDoS attacks
The first symptom of a DoS or DDoS attack is the slow response of the services. If your network traffic and other browsing have slowed down, hung, or frozen, it is likely that your endpoint is being flooded with illegitimate requests.
Other methods to detect and respond to DDoS attacks are through traffic monitoring. If a certain IP address is sending an absurd amount of requests, then the chances are that it is a DoS attack. Also, unusual traffic spikes can be observed during an attack.
For these purposes, you must use special types of monitoring and alerting tools so that you or your security team can respond in a timely fashion.
Password attack
A password attack is where an attacker gains unauthorized access to your digital property simply by gaining access to your password (and other associated credentials). They can either guess the password, by using the most common passwords like “qwerty” and “1234567,” or do phishing scams to get you to tell them their password.
Phishing, dictionary, keylogger, and brute force attacks are types of password attacks where the hackers try to log into your account(s) by securing or guessing your password. There are also other, more serious password attacks with high penetration chances, like password spraying and Main-in-the-middle attacks.
Alternatively, a hacker can also attempt to crack your password using various tools, like Cain and Abel, John the Ripper, etc. Regardless, access is gained by using your legitimate credentials to break into your account.
Detecting password attacks
Typically there is no intimation of a password attack, since the attacker logged in using legitimate means, even if they acquired the password illegally. Therefore, you may not become aware of a password attack until it is too late.
You will probably realize that your password has been compromised when you receive a notification of a new device login, or when an action is performed by the attacker which you did not do or authorize, for example, posting on a social media website without you knowing about it.
Structured Query Language (SQL) injection
SQL injection is performed on servers holding SQL databases, including web servers. These types of attacks only target the components that are database-driven and penetrate into the databases. The attacker is then able to manipulate SQL queries and make changes to the database tables, including adding, modifying, and removing them.
Usually, a malicious piece of code is inserted into a data plane, like a text field, and then when a user interacts with that field, their system is penetrated and hence, compromised.
A malicious code injected onto a web page can be for any intentions and purposes. An attacker could create a back door to your device, or plan a spyware on your PC and monitor your every move.
Detecting SQL injection
Once an SQL injection has taken place, there is no other method to detect it other than performing a manual code check of the entire application. Therefore, if you fear that your web application is compromised from the backend, then you may want to sit down for this long process of scrutiny.
However, security professionals advise testing a web application for SQL injection vulnerability before making it public. Such tests are performed to check for any possible exploits that a hacker can use to inject their code.
Domain Name System (DNS) tunneling
The Domain Name System is a way to translate human-friendly URLs into machine-understandable IP addresses. DNS tunneling refers to the malicious intent of a hacker who creates a Virtual Private Network (VPN) connection with an end device, usually behind a secure firewall, and their own server.
This kind of attack uses a DNS server to establish the connection and also uses port 53, which is the standard port for DNS traffic.
For an attacker to successfully implement a DNS tunneling attack, they must first register a domain. The domain’s name server will then point to the hacker’s server, where the tunneling malware is installed, and any visitor will automatically get their device infected. The attacker would then be able to connect to the target PC using the malicious tunnel, even if it sits behind a firewall since no traffic will be detected within the VPN.
Detecting DNS tunneling
Detecting a DNS tunnel is not a very straightforward process. Since everything is happening in the background, it may go undetected if the attacker does not perform any obvious malicious activity. However, security professionals can use specialized tools, like DNS monitoring and payload analysis utilities to keep an eye out for unusual network activity.
Zero-day attack
Zero-day or 0-day attacks are attacks carried out by hackers on a vulnerability that has been publically announced. For example, when a software vendor finds out that there is a security vulnerability in their software, it publishes an announcement of the vulnerability so that the users are aware and can secure themselves. However, this announcement also falls on the ears of the attackers.
The attackers then attempt to exploit the vulnerability before it can be patched by the vendor.
This is called a zero-day exploit since everyone is just learning about the vulnerability, and on the same day, the attackers jump in to take advantage of the opportunity.
Detecting zero-day attacks
Zero-day attacks can exploit any vulnerability in a service or an application. Therefore, you may only be able to detect an ongoing zero-day exploit when your device has already been targeted.
There is no specific method to detect a zero-day exploit, except to keep an eye out for the announcement by the vendors, and always make sure that your devices and software are up to date with the latest security patches.
Cryptojacking
As you may notice, the word “cryptojacking” is closely related to “cryptocurrency.” Cryptojacking refers to gaining unauthorized access to other systems’ resources for the purpose of mining cryptocurrency.
Cryptocurrency works on the principle of blockchain – which is a chain of systems providing computing power. In exchange, they provide cryptocurrency to the associated accounts.
Hackers use malicious downloads or use drive-by attacks to infect websites, and then plant the malicious code onto the end devices. They then use the target PC’s resources for mining purposes, thus achieving a financial gain.
Detecting cryptojacking
Detecting whether your device is being used for mining cryptocurrency is relatively easy. Since your computer’s resources will be used in an absurd capacity, you feel that your computer is sluggish and lagging in performance.
If you feel that your computer has been cryptojacked, open the Task Manager and check if your CPU and GPU are being used more than they are supposed to. If you find that there are certain processes that are taking up the resources, and you do not recognize them, it is likely that your computer has been infected with a virus for mining purposes.
URL interpretation/poisoning
URL interpretation, also known as URL poisoning and URL manipulation, is a kind of attack where the hacker can access certain parts of a web application that are not supposed to be displayed or accessed. This is done by modifying the queries sent to the URL without changing the syntax.
In this method, the parameters of the query are manually changed and the query is forwarded to the URL. Then, the web server responds to the new query with information that is not supposed to be accessible.
Detecting URL poisoning
If there is a website that you want to access but fear poisoning, you can perform a generic search using any search engine and observe the results first. If a URL has been poisoned, you may see questionable results.
For example, while the title of the result states the name of the website, the fine text below might be showing in a different language, or display different information. This would indicate that the URL has been compromised.
Alternatively, you can also use scanning tools to search for certain URLs, and these tools will scan the URL for any malicious content and report it.
Birthday attack
The name for the birthday attack originates from the birthday paradox. This is based on the story of an XXX amount of people present within a room, where each of them thinks that they have a unique birthday, different from all the rest. However, the chances of at least 2 of them having the same birthday is more than 50%, statistically.
The same concept applies to the birthday attack, where an attacker manipulates the authentication mechanism between devices, known as the “hash algorithms.” This is a type of cryptographic attack, the same as cryptojacking. However, it is not necessary that the attacker will get a financial gain.
Although hash algorithms are part of a security feature to authenticate whether the data received is from the genuine sender, attackers can easily manipulate them and make the receiving device think that the data is legitimate, whereas it has been changed by the attacker.
This happens as the attacker has successfully created the same hash algorithm as the authentic message, making the receiving device believe that the data is authentic as well. However, that is not the case any longer. The original data packets have been intercepted by the attacker and replaced.
That being said, the chances of the attacker creating the same hash algorithm as the original are also high, hence the name “birthday attack.” In fact, it also has a mathematical formula for calculation based on the yearly number of days (365).
Detecting birthday attacks
To detect a birthday attack, you must have significant knowledge of packet inspection and algorithms, since the only method to detect if you are being attacked using a birthday attack is by inspecting the data packets themselves.
If you find any anomalies inside the packets, and the data inside the packets is not what it is supposed to be, then you would know that the algorithm has been duplicated to feed false information.
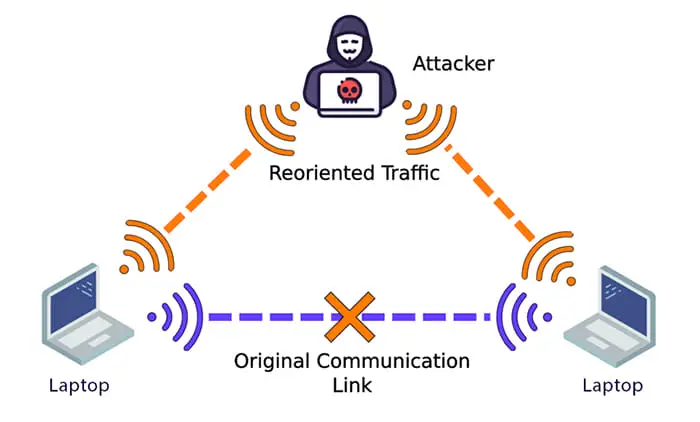
Man-in-the-middle (MITM) attacks
As the name implies, a man-in-the-middle attack is when the attacker places themself in the middle of two communicating parties. This is an eavesdropping attack where the session is usually hijacked by the hacker.
The attacker then pretends to be a legitimate party and communicates with one or both of the devices pretending to be someone else. These can be both network or system attacks.
A MITM attack can be horrendous depending on the type of session the attacker has hijacked, and what information is being exchanged within the packets.
Detecting man-in-the-middle attacks
Usually, MITM attacks cannot be detected with the bare eye, since they hijack a legitimate ongoing session. Therefore, you need to use specialized tools like Deep Packet Inspection (DPI) tools, IDS and IPS, etc. Moreover, you can also monitor the latency of the incoming and outgoing packets, and check how long it takes the attacker to replace the original packets.
Closing words
As we mentioned at the beginning of this article; it is important to understand the many different types of cyberattacks so that you are aware of how they can be detected, and thus, devise a foolproof security plan to mitigate it before an incident even occurs.
That being said, each of the aforementioned cyberattack types in this article has subtypes. Therefore, there aren’t only 16 types of cyberattacks, but much more. These have been defined in individual posts for each type of cyber attack linked in the article above. To learn more about the cyberattack, simply go to the dedicated posts.