Are you finding irregular activities on your computer, like finding software that you did not install, unwanted ads and popups, or abnormal use of system resources? If yes, then it is likely that your computer has been infected with malware.
Malware, which is the condensed form of “malicious software,” is intrusive software created to harm you, your assets, and digital data, or benefit its creators in any way (usually financially).
There are many sorts and forms of malware. Some might be easily detected, while others are designed to remain incognito for as long as they can. Every type of malware has a different agenda and thus works differently.
In this article, we are going to discuss all the types of malware, and everything there is that you need to know about them, including protection techniques. The knowledge of each malware type can benefit you in protecting your assets better.
Learn how to protect your devices from all sorts of malware attacks.
This page covers
What is malware?
The word “malware” has been derived from the words “malicious software.” Malware is a generic word used for specialized, malicious software or code intended to inflict harm to an individual or an organization. Through that harm, the attacker, who is usually the creator or deployer of the malware, may or may not benefit.
Malware has many different types. It can be designed to attack individual systems (computers and devices), or entire networks. They can create back doors for future access for the attacker, steal information, propagate through the network automatically, encrypt or remove data permanently, and much more.
A malware attack can have one or more of the following intents:
- Gather intelligence: Steal information that the attacker can later leverage or sell on the black market.
- Cause disruption: The attacker only wants to disrupt the target’s business, or uses it as a distraction for an ulterior attack.
- Extort money: The attacker may steal the target’s information or encrypt their data, and may only offer to fix it in exchange for money.
- Consume system resources: The attacker plants bots (pieces of code) to use your system resources for malicious purposes, like mining cryptocurrency or performing DDoS attacks.
- Generate revenue: The attacker can plant adware for you to interact with ads, which in turn will provide monetary gain.
Types of malware
Ransomware
As the name implies, a “ransomware” attack involves the attacker asking for a ransom amount from the target in exchange for getting their data back. Normally, the attacker encrypts all the data on the hard drive of the target device and then demands a sum of money which the target has to pay if they want their data back and unencrypted.
Sometimes, if the information is important to the victim, they oblige with the demands and pay the amount. However, they rarely hear from the attacker again and do not get a decryption key even after making the desired payment.
That said, ransomware attacks have been modified over the years to inflict even more harm, such as stealing information.
Ransomware attacks have become quite common over the last decade. Not only have the attackers targeted individuals, but also businesses and healthcare organizations.
Types and examples of ransomware attacks
There are only two main kinds of ransomware attacks, which are as follows:
-
Encryption ransomware
In this type, the victim can log into their account and access the computer. However, all of the files and folders will be encrypted and inaccessible. In this case, no security software can decrypt or access the data.
-
Screen-lock ransomware
In this type of attack, the victim is unable to use the computer entirely. As soon as they start the computer, they see a message screen demanding the ransom, and may even include the consequences if the ransom is not paid. This kind of ransomware usually also encrypts the system files needed for the operating system to work.
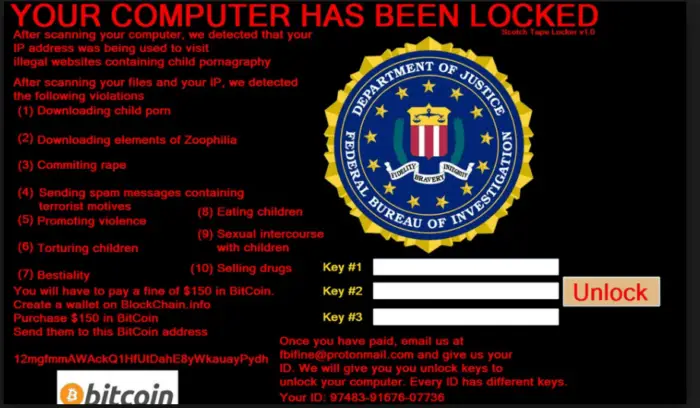
Screen lock ransomware example
Other than this, a ransomware attack may behave differently because it was developed by a different group. A type of ransomware attack is usually named after the group that created or operated it. Here are a few examples of certain types of ransomware attacks that caught the public eye over the last couple of years:
-
Ryuk
It is a targeted attack that is normally delivered through spear phishing, or remotely through compromised user credentials to access organizational resources. Once accessed, Ryuk encrypted certain types of files excluding the ones important for the OS, and then displayed a ransom note.
The Ryuk ransomware attack cost well above $1 million to the victim organizations.
-
Maze
Maze was the first ransomware attack that also stole data. It was developed as a failsafe in case the victim did not pay the ransom money, which the attackers then used to blackmail the victim for leaking their data or selling it to the highest bidder in the black market.
Although the group operating the Maze attack has ended its operations, it allowed other groups to create variations of the attack, like Egregor and Sekhmet, which are still operational today.
-
REvil (Sodinokibi)
REvil is a Russian group that targets large organizations with ransomware attacks. This is a notorious attack that competed with the Ryuk ransomware attack with respect to popularity and impact. It is reported that REvil occasionally demanded $800,000 from large companies.
-
Lockbit
Lockbit is another notorious ransomware attack designed to propagate quickly through organization networks and devices so it can inflict maximum harm without being detected.
Although a Russian has been apprehended for their involvement in a number of Lockbit attacks, it is still unclear whether all the operators behind the Lockbit attacks are Russian.
-
Lapsus$
Lapsus$ is a ransomware attack that originated in South America. It has claimed to have targeted high-profile individuals as well as organizations, and claims to have broken into Nvidia, Ubisoft, Samsung, and other reclaimed brands.
The Lapsus$ group is notorious not only for extorting money but also for threatening to release sensitive information if the ransom amount is not paid.
The salient feature of the Lapsus$ attack is that it masks itself as a legitimate process running in the background whilst it encrypts your data.
-
WannaCry
WannaCry is a ransomware attack that also automatically propagates throughout the network after scanning for vulnerable devices. In other words, it was a ransomware attack that was also a worm.
It uses the EternalBlue exploit, created by the United States National Security Agency (NSA) for legitimate purposes, which was later leaked for malicious purposes by the “Shadow Brokers” group.
This attack targeted the Windows operating system throughout organizations making them paralyzed and inoperable. Although Microsoft released a patch that mitigated the vulnerability, the group targeted organizations that either did not apply the patch or the operating system versions had reached End-of-Life.
This was a planned attack carried out on 12th May 2017, across 150 countries simultaneously, that infected nearly 300,000 computers. The estimated damage was billions of dollars.
There are many other instances where a ransomware attack has made headlines in the news, but these are the more prominent ones, and of different kinds, so you get the gist of how many variations of ransomware attacks are there.
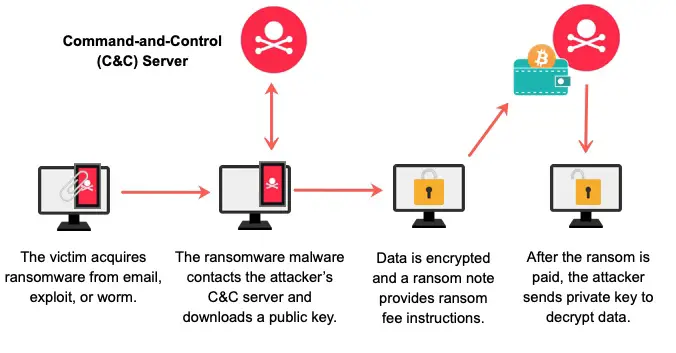
How ransomware attack works
Regardless of the type of ransomware attack, all of them have the same core operating steps. While some may have extra steps, such as performing network scans or stealing the data before being encrypted, the main steps are the same.
-
Gaining access
First, an attacker must gain access to the target computer. For that, they usually perform phishing techniques through spam emails which encourage the victim to perform an action, like downloading a file or opening an external link. This action normally results in the ransomware file being downloaded and executed on the computer.
Note that the attacker may also adapt other methods to access the computer. Normally, the other method involves accessing the computer remotely after cracking the password of a user account within an organization. Using those credentials, they are able to gain access using the Remote Desktop Protocol (RDP).
-
Encryption
The next part is the encryption phase. Once the attacker has gained access to the device, all they need to do is execute the malicious code. It will then begin encrypting select data and replacing the accessible content with a ransom note.
Some encryption software may also delete shadow copies and backup files so that the victim is unable to recover any data, forcing them to pay up.
-
Demand ransom
Once the data has been encrypted and the ransom note is left behind, all the attacker needs to do is wait for you to comply. Typically, these notes demand a set amount of cryptocurrency in exchange for access to the victim’s files.
Once you have paid the amount, the attacker should provide you with a decryption key, which you can then enter into the encryption software (also created and planted by the attacker) to retrieve your data. However, note that the practice of sharing the decryption key is becoming uncommon, and the victims are left with encrypted data even after paying the ransom amount.
How to protect against ransomware
Here are a few things you can do to protect your assets from ransomware attacks:
- Beware of phishing/social engineering schemes
- Use secure authentication methods
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Use encryption
- Avoid public networks
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Enable/use firewalls
- Regularly backup data
- Reduce attack surface
- Enable controlled folder access
- Monitor network traffic
- Use honeypots
- Use Access Control Lists (ACLs)
Spyware
By definition, spyware is a type of malware that installs on a computer without the user’s consent, steals information, and then sends it to a third party, without being detected. Spyware can be installed on a computer as a standalone software, or bundled together with another legitimate software that you intentionally installed.
The primary purpose of spyware is to infiltrate your computer or network, fetch as much information as it can, and then communicate it back to a third party. This third party can be the creators of the spyware, advertisers, or data collection firms who auction off your data to the highest bidder. How the data is then used depends on the type of third party.
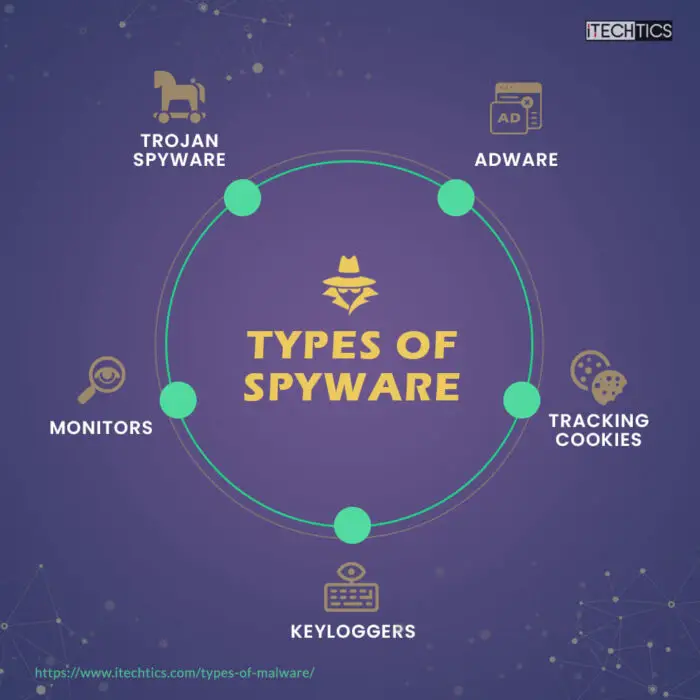
Types of spyware
As with ransomware, there are also different types of spyware based on what it is capable of. Here are a few examples:
-
Trojan spyware
Trojan spyware piggybacks on legitimate software bundled together with malicious code. Usually, a hacker creates a useful program, binds spyware to it, and then silently installs both of them on your PC. While you may allow the legit software to be installed, you may not be notified about the other silent installation of the spyware.
-
Adware
Adware is also a kind of spyware that monitors your data, including web surfing, and sends the data back to advertisers so that they can use that information for more targeted advertisements. Moreover, the adware may also pop up malicious ads for you to interact with based on the data it has already obtained from your device.
-
Tracking cookies
Cookies are used to track and monitor your information on the web. A hacker may plant cookies on your PC so that they, too, can track your browsing patterns and then get their hands on that information.
-
Monitors
Monitoring spyware’s only job is to monitor your every move. They typically record your activity on the system, and the sites you have visited, store your credentials, and then communicate them back to the attacker. Keyloggers are also a type of spyware.
-
Keyloggers
Keyloggers are software (or hardware) that capture each keystroke the user makes. These are then communicated back to the attacker using which they can steal sensitive information to blackmail the victim, sell to the highest bidder, or gain financial benefit.
What information does spyware capture?
Spyware has no interest in information it cannot use against you, or sell to someone who can benefit from it. Therefore, they are usually targeted toward gathering and reporting the following data:
- Sensitive and personal information
- Login credentials
- Account PIN/password/patterns
- Financial information (like credit card numbers)
- Keystrokes and other input
- Track browsing patterns and history
- Extract email addresses
How spyware works
There are three main steps in the functionality of spyware.
-
Infiltrate the system
The first thing for the attacker to do is infiltrate your system and deploy the malicious software. To do that, they can use multiple means, such as bundling the spyware together with legitimate software so you install both without even noticing.
Another method to deploy spyware is through spear phishing via malicious emails. When a user clicks on a link inside such an email, the spyware is automatically downloaded and executed. Once the spyware is deployed, they usually use common process names to disguise themselves as legitimate OS processes so they can function without the user noticing.
-
Monitor and capture
The next phase of the process is monitoring and recording the user’s activity and other information. Some spyware may be stealing the stored information on the hard drive, some may be logging the keystrokes and monitoring web activity, while some may be doing both.
Spyware may be observing and recording this information all the while performing the next phase as well.
-
Sending data
Another purpose of the spyware is to send the data to a third party; most likely the attacker, since the recorded information is of no use if it is not shared with the third party. Therefore, the software is programmed to communicate the gathered information remotely over the internet with the attacker.
Once gathered, it is up to the receiver how to use that information. They may use it to extort money from the victim or sell it to the highest bidder.
How to protect against spyware
Here are a few things you can do to protect your assets from spyware attacks:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Increase internet security level
- Close listening ports
- Enable/use firewalls
- Do not accept cookies
- Monitor network traffic
- Use Access Control Lists (ACLs)
Adware
An adware secretly installs itself on a computer, or a mobile phone, and displays unwanted advertisements which in turn generate revenue for the developers/attackers. Adware also falls under the “spyware” category if it is programmed to collect information as well for advertisement or other malicious purposes.
Adware can track your online browsing movement and send that data to the attacker. They can then sell that information to the advertisers, or use it themselves to show you targeted ads.
Adware can show you advertisements inside an app, or in the form of annoying popups. Depending on the type of adware, the attacker can have monetary gain when you click on it or even view it.
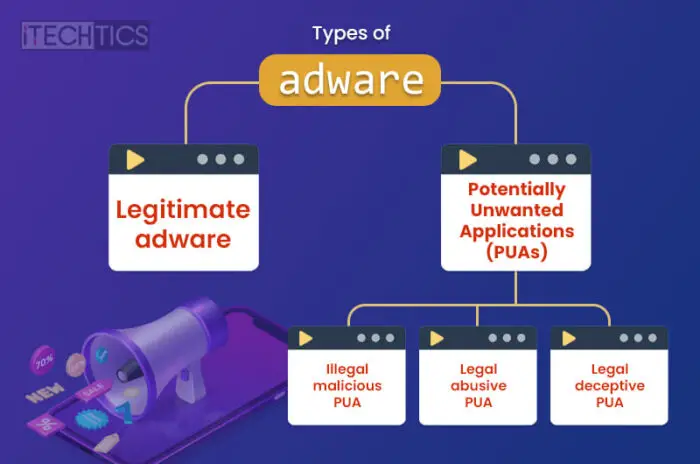
Types of adware
There are different types of adware infecting computers. Here are the major types of adware:
-
Legitimate adware
A legitimate adware is one that you install with consent. This kind of adware is used to compensate for the developer cost of a program that you acquire for free. Moreover, the ads in such software are non-malicious and usually accurate.
Even the most reputed developing firms include adware on some of their software products to cover the costs of the project. These are legitimate adware that the user knowingly installs and agrees to.
-
Potentially Unwanted Applications (PUAs)
As the name implies, Potentially Unwanted Applications, also referred to as Potentially Unwanted Programs (PUPs), are software that you did not intentionally install. These can be installed when you accidentally, or deliberately, click on a malicious link or are bundled together with another legitimate app.
PUAs come in different types, While some may not be entirely illegal, they still fall into a gray area. Here are the different types of PUAs:
-
Legal deceptive PUA
These types of adware are legal provided that the creator of the legitimate software unknowingly included ads that contain malware. Software that makes it tricky to opt out of installing adware also falls into this category.
-
Legal abusive PUA
The adware that bombards you with non-malicious ads falls into this category. The adware may flood your screen with advertisements, they are considered legal (sort of) as long as they do not contain any malicious or illegal content.
Such software may show ads in popups or as toolbars in web browsers.
-
Illegal malicious PUA
These are the worst kind of adware. Malicious content is deliberately placed in ads so that the victim’s device is compromised as soon as they click on the ad. The ads can include malware, viruses, and directions to malicious websites.
These are illegal adware since the creators knowingly inflict harm to the victim’s assets and data.
-
How attackers benefit from adware
When it comes to adware, the benefit for the attackers is always financial. They profit from the companies for which they are displaying the ads. The creators of such adware make money from such third parties using the following means:
- Pay-per-click (PPC): The creators of the adware are paid each time a user clicks on the ad.
- Pay-per-view (PPV): The creators are paid each time an ad is displayed.
- Pay-per-install (PPI): The creators are paid each time the software is installed on a device.
How adware works
By now, the functionality of any adware should be pretty straightforward.
The first thing an adware needs to function is to install itself on your computer. That is done by bundling the adware with another legitimate software or tricking a user into clicking on a malicious link through email phishing. Either of these methods will install the adware on your PC.
Once installed, all the program needs to do is display ads. The methods to display them can vary depending on the type of adware. While some may appear in the form of additional toolbars in web browsers, others may randomly show popups with ads.
Now, depending on how the creators of the adware generate revenue from the ads (PPC, PPV, PPI), they will start profiting off of it. They will profit until you remove the adware from your computer.
How to protect against adware
Here are a few things you can do to protect your assets from adware:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Adjust browser security settings
- Enable SmartScreen
- Do not connect untrusted storage devices
- Increase internet security level
- Use adblockers
- Purchase ad-free devices
Virus
A computer virus is a kind of malware that spreads between different computers. It is different from typical malware as a computer virus needs to attach itself to a host, much like a biological virus does.
The purpose of a virus is the same as any other malware – causing disruption and chaos. However, they are designed to propagate from one device to the next by attaching themselves to other files and folders.
How does a computer virus spread?
A virus only spreads once it has infiltrated a system, and an action is performed by the user. For example, if a virus has attached itself to a file, and the file is shared via email, the recipient device of the virus-attached file will also be compromised when the virus is executed on it.
Similarly, a virus may also spread when other mediums are used to share corrupted files and folders. A classic example of such a virus is the USB shortcut virus, which creates shortcuts for all files on the USB and makes the actual files inaccessible. this virus also propagates from device to device when the malicious file or folder is copied to/from the USB flash drive.
Note that a virus does not spread on its own. It requires the following things to spread:
- A host program.
- User input/action.
- Replaces legitimate files or attaches itself to legitimate files.
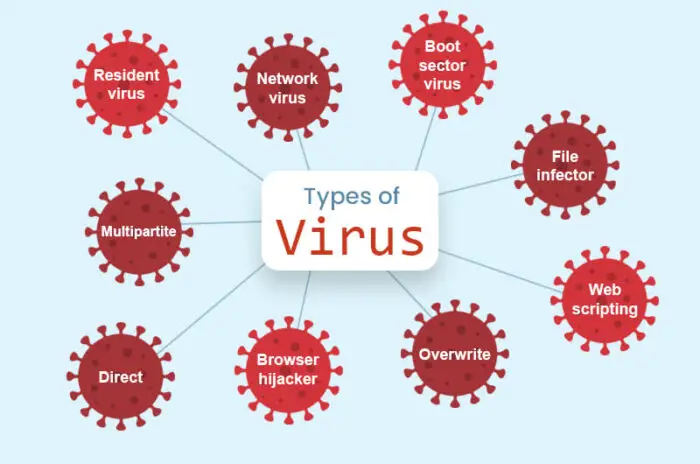
Types of computer viruses
There are different types of viruses that are categorized based on their behavior. Here are a few common types:
-
Resident virus
A resident virus infects an app or program as they are being launched by the user. They then propagate across all other applications as the user continues to open and access them.
-
Multipartite virus
A multipartite virus uses multiple ways to infect the computer. Its primary target is to compromise the hard drive and everything on it, which it does while remaining on the computer’s memory. It then propagates to other connected hard drives by altering the content within the application.
-
Direct action
A direct-action virus has the potential to destroy the computer’s hard drive and any attached storage device. It accesses the computer’s main storage and infects all of the apps, programs, files, and folders located in the “Autoexec.bat” path.
The Autoexec.bat is a batch file used to set defaults and run programs at startup.
-
Browser hijacker
As the name suggests, a browser-hijacking virus only makes unauthorized changes to web browsers, like changing the home page, the new tab default page, etc. They are not exactly a virus as they do not directly affect the computer but can lead to other malicious websites using the compromised browser.
-
Overwrite virus
As the name implies, an overwrite virus overwrites the user’s files and folders, and depending on its severity, can also impact the critical OS files and folders. It replaces the original files with malicious files, and the original data is then lost forever.
Usually, the original data that has been overwritten is never recovered, and the only way to get rid of the virus is to delete the affected files.
-
Web scripting virus
A web scripting virus attacks the security protocols in place by different web browsers. Such viruses are usually created to make web pages vulnerable to other threats and attacks.
A scripting virus attacks the browser’s security and injects malicious code into the browser. When the browser accesses another website, it then injects malicious code onto the web page.
-
File infector
As the name implies, any virus that infects files is a file-infecting virus. These are usually designed to propagate quickly through the system and other devices once the compromised files are shared and executed.
This kind of virus normally overwrites the file as they are being accessed and opened.
-
Network virus
Network viruses concern the whole network as well as other systems on the network. These are also the most dangerous kind of virus since it is capable of crippling the whole network.
A network virus is relatively different to detect since the primary malware file can be hidden away on any system on the network.
-
Boot sector virus
A boot sector virus directly impacts the Master Boot Record (MBR) partition on the hard drive. This is a deadly virus that can crash your hard drive and prevent your PC from starting up at all.
The virus injects its code into a hard drive’s partition table, and then moves into the main memory when the computer restarts. Such viruses cause hindrances in starting up the computer, lower the boot performance, and sometimes prevent the system from starting up at all.
How a virus works
Like all malware, a virus must also reach its target computer. These are usually delivered through malicious practices as well, like attaching the virus with legitimate software, phishing emails, and downloading onto your computer when you click a link or unverified downloads.
When a virus enters a computer, it is not necessary it may start infecting the file(s) right away. It may be possible that the virus remains dormant until the right time. Moreover, it may also propagate through the system, or through other devices on the network, without showing its true colors and activating its malicious payload.
Then, the virus just waits to be activated. This can be done when a user triggers it, like opening an infected file. When the virus is executed, it releases a payload. In simpler words, the malicious piece of code is then executed, and the virus performs what it was designed to do.
Detecting a virus
While it can be pretty straightforward to detect some viruses; others, not so much.
On a single computer with a virus, you may observe one or more of the following symptoms:
- Degraded computer performance
- Corrupted, missing, or replaced files
- The computer won’t start
- Flod of popups
- Excessive use of the system memory and/or the hard drive
- Apps and programs are crashing
How to protect against viruses
Here are a few things you can do to protect your assets from computer viruses:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Reduce attack surface
Trojan
A trojan, or a trojan horse, is a type of malware that disguises itself as legitimate software but is actually malicious. Such malware is usually conjugated with another, legit app. This technique is referred to as “piggybacking.”
As you have already learned, trojan malware is classed as such because of its delivery medium, and not because of the type of attack, or the function it performs. That being said, there are different kinds of trojans.
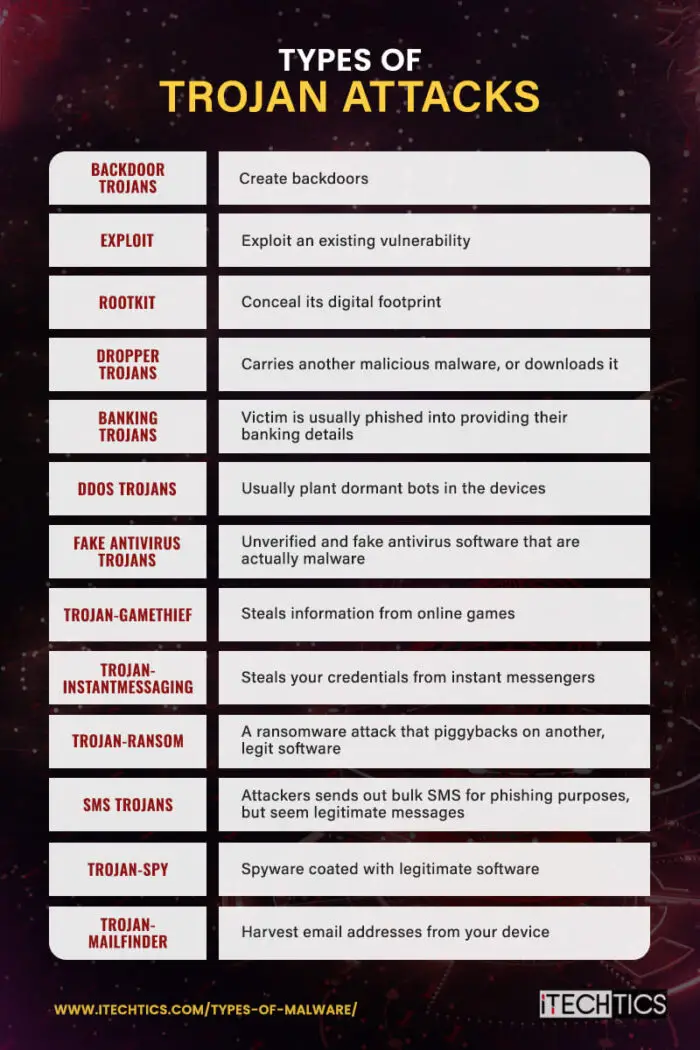
Types of Trojan attacks
The following are the types of trojan attacks:
-
Backdoor trojans
Trojans that create a backdoor to your system fall under this category. These are perhaps the simplest, yet the most damaging trojan kinds. In such an attack, the malware leaves a back door open for the attacker using which they can access your computer remotely, from anywhere, at any time, for any purpose.
-
Exploit
Trojans that exploit an existing vulnerability on your system or an app are called Exploit Trojans.
-
Rootkit
Rootkits are another kind of trojan that is delivered via legitimate software but are, in fact, malicious. This specialized trojan is designed to conceal its digital footprint so that the malicious piece of code or software can run for a maximum duration without being detected.
-
Dropper/downloader Trojans
Dropper and downloader trojans are two different kinds but have much in common. A dropper trojan is itself harmless. However, it carries another malicious malware with it and drops and executes it on the target PC. In contrast, a downloader trojan requires the internet to download the malware on the target PC.
-
Banking trojans
Yes, banking trojans have to do with banking. These kinds of trojans target victims for monetary gain. In such attacks, a victim is usually phished into providing their banking details and credentials, usually into a manipulated web page that looks almost legitimate.
Normally, gullible and security-awareness-lacking individuals fall for the attacker’s trap and end up providing their financial information.
-
DDoS trojans
Distributed Denial-of-Service (DDoS) attacks are when a network of bots attack a single device or network overwhelming it with traffic, that they become disrupted, inoperative, and inaccessible.
DDoS trojans usually plant such dormant malicious code into the computers, which are then activated remotely when the time of the attack arrives.
-
Fake antivirus trojans
These are the software that you download and install to protect your computers from malware, but end up hurting your computer instead. Therefore, it is always advised only to use legitimate and reputed antimalware.
-
Trojan-GameThief
A trojan that steals information from online games, such as their gaming tag, email, and other information, falls into the category of “Trojan-GameThief.”
-
Trojan-InstantMessaging
Software that steals your credentials from instant messengers, like MSN Messenger and WhatsApp, falls into this category. Of course, such trojans are also programmed to communicate this information back to the attacker.
-
Trojan-Ransom
This is a ransomware attack that usually piggybacks on another, legitimate software. An attacker may even create legitimate software for the users to download, and then attach ransomware to it.
This sort of attack encrypts all of your data and makes a demand for a ransom to be paid, failing which will lock your encrypted data forever. However, there is no guarantee that the attacker will provide you with a decryption key once the ransom is paid in full.
-
SMS trojans
SMS trojans, although rare, are still in play. In the FakeToken attack, which is an SMS trojan attack, an attacker sends out floods of text messages to expensive international phone numbers and disguises itself in the system as a standard SMS app. Moreover, the victim has to then pay for the receiving SMS out of their own pocket.
-
Trojan-Spy
This is spyware coated with legitimate software. Spyware is designed to capture your information, such as screenshots, web activity, and keystrokes while transmitting the information back to the attacker.
-
Trojan-Mailfinder
Such trojans harvest email addresses from your computer and report them back to the attacker.
The list of types of trojans does not end here. There are as many trojans as there are types of cyberattacks since a trojan is identified through its mode of delivery.
How trojan works
As mentioned earlier, a trojan attack is characterized by its mode of delivery. Any malware that is delivered on the back of legitimate software is considered a trojan.
The legitimate software is safe itself. It does not harm your computer. However, the attached piece of code or software that it delivers is the devil.
To begin, a user, who later becomes the victim, downloads a piece of code or software onto their PC. They then execute the file and run it on their computer, during which the malware is also executed. While the user is unaware of the activity occurring in the background, they continue to perform their normal functions.
Note that a trojan may also be delivered via other means, such as through phishing emails, or even USB flash drives.
Once the trojan is planted, it begins to do its work, depending on what type of trojan it is. It may also even consume the network or system resources.
Detecting a trojan
A trojan will most likely be detected when it is already too late. However, if you are using antimalware software, then it may be able to apprehend the unverified piece of code before it can be executed on the PC.
However, once your PC has been invaded with trojan malware, you may find the following symptoms:
- Slow system performance.
- overuse of system or network resources.
- Unwanted apps and programs are automatically installed.
- Ads and popups are showing up.
- You are getting redirected to malicious web pages.
How to protect against trojans
Here are a few things you can do to protect your assets from trojan malware:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Regularly backup data
- Enable controlled folder access
- Monitor network traffic
- Use Access Control Lists (ACLs)
Computer worm
Like trojan malware, a computer worm is also classified because of one of its characteristics, and not because of a special type of cyberattack.
When we talk about a digital worm, we do not refer to the invertebrate animal. Instead, this is a type of malware that can propagate across a network and infect other devices without the requirement for human input. Unlike the virus, a worm does not require a host, nor does it need an action to be performed in order to execute and spread it.
That said, a worm could contain any kind of malicious software, designed for any intents and purposes. However, they are usually spread using the same techniques as any other malware.
How worms spread
Just like any other malware, attackers adapt different techniques to spread a computer worm across a network. All they need is one vulnerable computer and they are in. Here are a few initial methods that they adopt:
-
Phishing
Spam and targeted emails often entice individuals to click on an attachment or a link within a spam email so that it would automatically download and execute the worm.
-
File sharing
File sharing over the network, like P2P file sharing, can often include worms and transfers from one PC to the next.
-
Networks
Worms are self-replicating and, hence can duplicate themselves across connected devices on the same network.
-
Instant Messengers (IMs)
Instant Messengers, like WhatsApp, can carry malicious links and URLs, which redirect the user to a web page that downloads and executes a worm onto your device.
-
Externally-connected devices
External storage devices, like USB flash drives and external hard drives, can carry computer worms from one device to another without attaching themselves to a host.
What does a computer worm do?
As previously mentioned, a worm can do pretty much anything, depending on how the attacker programmed it. Here are a few things it is capable of:
- Drop other malware
- Take up the bandwidth
- Delete/replace your files
- Steal your data
- Create a back door
- Take up your hard drive
How computer worms work
The first thing the attacker focuses on infiltrating a computer. To do that, the attacker needs you to interact with one of the malicious devices, links, or URLs. So they might send you a phishing email, which may seem legit, but actually contains the worm. If you interact with the malicious code and accidentally download/install it on your PC, then your device is compromised.
Once a worm has made its way to your computer, it may or may not perform malicious activity. For example, some worms only create ridiculous amounts of copies of themselves to consume system resources and hog up the storage space. However, an attacker may program it to create a back door, steal or encrypt your data, or pretty much everything else.
While a worm performs its actual function, they are also programmed to scan the network once it penetrates into a new device. This is how a worm propagates on its own across different devices on the same network.
A worm may look for a vulnerability in a specific transmission protocol, and see which of the computers on the network are using that protocol. If detected, the worm might exploit it and infect the remote computer as well.
Detecting a computer worm
Worms are designed to perform their functions in the background, go undetected, and also propagate across the network without user input. Therefore, detecting them could be a bit difficult, unless their function isn’t very obvious, like popping up ads.
Therefore, here are a few things you should look out for:
- Monitor your free storage space on the hard drive.
- Monitor network consumption.
- The computer hangs or freezes often.
- The files are missing or corrupted.
- Windows Firewall is throwing up alerts.
How to protect against worms
Here are a few things you can do to protect your assets from computer worms:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Use encryption
- Avoid public networks
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Regularly backup data
- Enable controlled folder access
- Monitor network traffic
- Use Access Control Lists (ACLs)
Rootkit
The term “rootkit” originates from the Linux and Unix operating systems. The most privileged account on these operating systems is “root” (like it is “Administrator” on Windows), and the application that allows unprivileged access to the root account is named “kit.”
The rootkit attack is a sophisticated attack that operates on the kernel, or near the kernel, and provides all kinds of privileges to the attacker remotely. They gain complete access to the target computer. Additionally, rootkits are also programmed to cover up their attacks, so they can continue to perform their attack without being noticed.
Although rootkits are usually programmed so that they only affect the software and the operating system, some are so advanced that they also affect the system’s firmware and the computer’s hardware.
A rootkit can be programmed to perform different functions, like stealing the data, encrypting it, dropping or installing malware, or planting a bot to perform DDoS attacks. While rootkits may often be bundled into a single software, occasionally, they are split across two or more tools which further enhances the attacker’s illegitimate abilities over your PC.
How rootkits spread
Like most other types of malware, a rootkit is also spread and deployed using phishing techniques. These are usually spam emails where the target user accidentally (or deliberately) clicks on the malicious code or button.
Another common method for spreading rootkits is by exploiting a vulnerability of software. This then becomes a gateway for the attackers to plant the rootkit.
A simpler method is bundling the rootkit malware with other legitimate software or files.
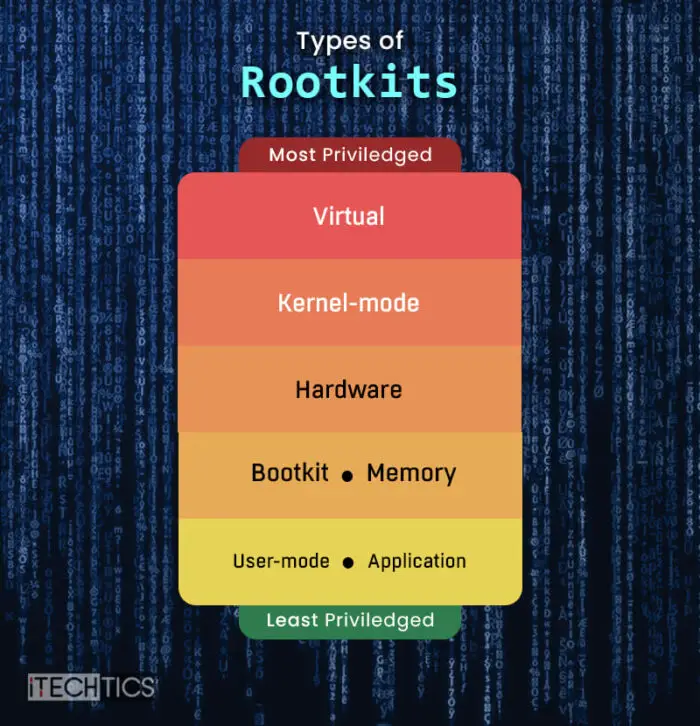
Types of rootkits
The attackers use different kinds of rootkit attacks, depending on what they want to achieve with it. Here are all the different kinds and their details:
-
User-mode rootkit
Regular rootkits that only affect processes, network connections, files, events, and system services are user-mode rootkits. These are the least-privileges rootkits with very minimal impact. However, these are still a threat to the system and also the network.
-
Hardware/firmware rootkit
This kind of rootkit directly affects your system’s hardware, including the hard drive and memory modules. Moreover, they can also affect the computer’s BIOS, which is the computer’s firmware.
This gives the attackers administrative control over your PC and can use it however they like, without being detected, which makes these kinds of rootkits the most dangerous ones.
-
Bootloader rootkit (Bootkit)
Your computer’s bootloader is responsible for loading the system resources to start it up. A bootloader rootkit replaces the original bootloader with the malicious one, and the malware is loaded even before the computer starts.
-
Memory rootkit
Memory rootkits live and execute inside the computer’s RAM, which is a volatile memory. This means that a memory rootkit is also lost as soon as the computer restarts. This is why a memory rootkit is not often considered a significant threat. However, sometimes, some additional work may be required to eliminate it.
-
Application rootkit
Such rootkits affect individual applications, like Office, paint, etc. Whenever a target opens these affected applications, the attacker gains control over your computer, but in the background.
These rootkits are often difficult to detect with the naked eye but can be eliminated with the help of antimalware tools.
-
Kernel-mode rootkits
The kernel is the functionality core of a computer. It is the main point of interface between the computer’s hardware and the operating system.
A kernel-mode rootkit attacks and infects the kernel of the computer, and is thus also one of the most dangerous kinds of malware. Such attacks do not only allow them access to your data but can also make changes to the operating system’s behavior.
-
Virtual rootkits
Virtual rootkits are executed under the original operating system and then hosted as if it were a guest OS. This allows the rootkit to intercept all hardware calls and modify them as it pleases. Note that virtual rootkits do not need to modify the system kernel, and are thus very difficult to detect.
Detecting rootkits
As you may have already learned, detecting rootkits may not be such a straightforward process as most other malware. Therefore, you may have to keep a keen eye on irregular computer activity. Here are a few things to look out for:
-
Blue Screen of Death (BSoD)
You may encounter an unusual amount of BSoDs. If you cannot fix them using the specific error code, then you may have a rootkit infection on the system.
-
Abnormal browser behavior
You may see bookmarks and additional toolbars in web browsers that you did not add.
-
Sluggish system performance
The system might seem ridiculously slower than usual.
-
Automatic changes in Windows settings
You may observe changes within the Windows settings that you did not make.
-
Irregular functioning of web pages
Web pages, especially the clicks, may not behave normally due to the flooding of network traffic.
How rootkits work
Like all malware, a rootkit first needs to be injected into your computer. This is normally done through phishing emails and other social engineering techniques. Once the malware has been planted, the user may execute it unknowingly. This will trigger the rootkit to run its malicious code.
When the rootkit malware is executed, it will release and execute the payload and perform its specified function. It may or may not infect the system’s firmware. Regardless, you will probably not know of the malicious activity at the time as it will be happening in the background. Moreover, rootkits are designed to cover up their tracks.
Now, your system will be in the control of the attackers and you may have to perform phenomenal steps to get rid of the malware from your PC.
How to protect against rootkits
Here are a few things you can do to protect your assets from rootkits:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Use encryption
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Regularly backup data
- Reduce attack surface
- Enable controlled folder access
- Monitor network traffic
- Use honeypots
- Use Access Control Lists (ACLs)
Keystroke logging
Technically, keystroke logging isn’t malware, nor is it an attack. It is the misuse of a specific kind of software (or hardware) that makes it malware. More specifically, keystroke logging is considered spyware.
A keystroke refers to the press of a key on your keyboard. It is what you use to interact and communicate with the computer. Depending on what key was pressed, its longevity, and its combination, the computer performs a certain function. Keystroke logging, as the name implies, is logging (or recording) the keystrokes a user performs.
Keystroke logging may be considered legal if it is being used for the right intents and purposes, such as monitoring the productivity of your employees in a work-from-home scenario. In this case, the keystroke logger – the hardware/software that logs and communicates the keystrokes – must be installed with the consent of the user.
However, when used for malicious intents, a keystroke logger is never installed with the user’s permission. Instead, it is deployed without them knowing about it. This way, an attacker quietly installs a keylogger (short for “keystroke logger”) on a target PC and then continues to monitor whatever they are typing into a computer.
This way, an attacker can gain access to all the secrets of the user, including their online activity, what they are typing in emails, their usernames and passwords, and everything else that is pressed on the keyboard.
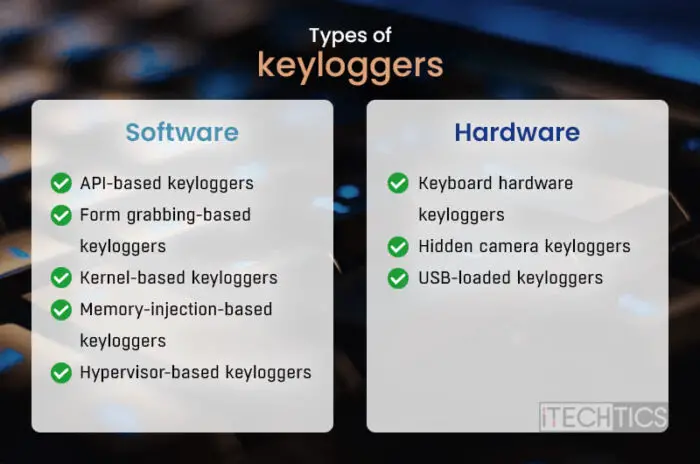
Types of keyloggers
There are two main types of keyloggers:
-
Software
Software keyloggers are applications and programs installed into the computer. It also has different kinds:
-
API-based keyloggers
Application Programming Interface (API) allows software and hardware from different manufacturers to communicate with one another. API-based keyloggers listen directly to the keystrokes sent from the hardware to the application using such APIs by eavesdropping.
-
Form grabbing-based keyloggers
These kinds of keyloggers intercept all text that is entered into web forms online. The data is first stored locally before being sent to the web server.
-
Kernel-based keyloggers
Such keyloggers gain access to the system’s kernel for administrative privileges, which allows them to log all keystrokes across the whole computer.
-
Memory-injection-based keyloggers
These programs modify the memory tables associated with the web browser in order to carry out their recording.
-
Hypervisor-based keyloggers
These keyloggers can stay hidden under the original OS in a malware hypervisor and record all keystrokes being sent from the keyboard to the apps and programs.
-
-
Hardware
Hardware keyloggers are devices that are usually connected to your computer to record the keystrokes. There are even some devices that may not need to be connected to your PC directly in order to record the keystrokes. Here are a few hardware keylogger types:
-
Keyboard hardware keyloggers
These devices are usually connected in series with the keyboard and record the keystroke before sending it off to the computer.
-
Hidden camera keyloggers
These are cameras, usually placed in public places, that visually track and monitor your keystroke activity in secret.
-
USB-loaded keyloggers
These are devices, such as USB flash drives, that are trojan malware and send your keystroke data to the attacker while the device is connected to your PC
-
How keylogging works
Keylogging requires either hardware or software to be installed on the computer. Although possible, hardware keyloggers are not used very much since they require physical access to the PC by the attacker. Therefore, they prefer using software keyloggers.
Software keyloggers are usually delivered through phishing emails, and intimations to update their software. A gullible user then may click on the malicious link which will plant and execute the keylogger on the system.
Once the keylogger is deployed, all keystrokes are recorded by the program and communicated to the attacker. Depending on the sophistication of the keylogger, this data can be in ASCII code, regular alphabets, or a series of key keys and combinations. Regardless, they are usually unencrypted and readable by the attacker.
The attacker can then use this information to gain unauthorized access to websites, extort money from you, or sell your information to the highest bidder.
How to protect against keylogging
Here are a few things you can do to protect your assets from keyloggers:
- Beware of phishing/social engineering schemes
- Use secure authentication methods
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Do not connect untrusted storage devices
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Monitor network traffic
Backdoor attack
A backdoor attack occurs when the attacker creates a backdoor to your system, a specific application, or the OS.
Think of this digital backdoor as a physical backdoor to your house. You may have several security measures in place, such as a guard dog, security cameras, locks, and an alarm system. But there is an underground tunnel using which anyone can get in and out of the house without getting detected. A digital backdoor works in the same way.
You can define a backdoor that provides alternate access to something while bypassing the usual security checks in place.
Are all backdoors malicious?
Not all backdoors are malicious. It basically depends on what the backdoor is used for.
If an attacker is using a backdoor for malicious intents, such as stealing data or planting more malware, then it is a malicious backdoor and should be sorted out immediately. However, attackers aren’t the only ones who create backdoors.
Some software and hardware manufacturers create backdoors into their own systems for troubleshooting purposes. These are usually used by the company themselves in case they need to patch the firmware, update the software, or grant a user access if they find themselves completely locked out. In this case, the backdoor cannot be considered dangerous.
That said, if an attacker becomes aware of an existing backdoor that was created by a prior attack, or created by a manufacturer for legitimate purposes, they could potentially exploit it and gain access themselves.
What are backdoors used for?
As previously mentioned, backdoors can be used for both legitimate and malicious intents. Here are some of the uses for a digital backdoor when it is being used for the wrong reasons:
- Stealing data
- Accessing the computer remotely on demand
- Planting and executing more malware
- Decrypting data in a ransomware attack once the demands are met
- Executing DDoS attacks on demand
- Performing fraudulent transactions
- defacing websites
How backdoor attacks work
Initially, backdoors need to be planted and created. These can be delivered to the target PC in various ways. Normally, attackers use conventional methods to infiltrate a target PC, like phishing emails, attaching malware with legitimate apps and programs, etc.
Once the malicious piece of code is executed on the computer, it can create a backdoor through a vulnerability in software or within the OS. The attacker would then know that they can now access your computer remotely while bypassing all the security checks in place.
Types of backdoor attacks
There are various kinds of backdoor attacks, each with its own intent. Here are a few examples:
- Cryptojacking: This kind of backdoor attack mines cryptocurrency using your system resources.
- DDoS attack: Normally, a backdoor is created to use your system as one of the attacking devices for a DDoS attack.
- Ransomware: A backdoor is left open so the attacker can access the computer to decrypt the locked/encrypted data.
- Spyware: A spyware’s backdoor relays the captured information to the attacker in secret.
- Trojan: A trojan horse can create a backdoor for many purposes while disguising itself as legitimate software or process. It normally allows remote access for the attacker.
How to protect against backdoor attacks
Here are a few things you can do to protect your assets from backdoor attacks:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Use encryption
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Reduce attack surface
- Use adblockers
- Purchase ad-free devices
Bot/botnet attacks
A botnet is a collection of bots. The word “botnet” is derived from “robot network.” A bot is actually a piece of code injected within a computer that can perform a number of different tasks, as designed by the attacker.
In a botnet attack, the attacker is also referred to as the “bot-herder.” They use bots to perform tasks that otherwise would be impossible. This is because botnet attacks give the attackers the power of thousands of devices if not millions.
Bots are used to perform different kinds of attacks. They are usually silently injected into the target computers and remain dormant unless called upon by the bot-herder. These are also called zombie computers.
For example, bots can be deployed to perform a DDoS attack on a specific server. When triggered, they will all send requests, in millions, to the same server, rendering it incapable of performing any other task. However, the bots do not become useless once they perform a task. They can now be updated to target another server or change their purpose altogether.
The bot-herder can also change the bot’s behavior with a single update and get it to perform another kind of attack. Even if they have no direct contact with a zombie PC, they can use other bots to propagate an update onto other zombie computers, creating a communication mesh.
This is how bot herders usually rent out their botnets to other attackers for financial gain.
How botnet attacks work
The first step, like all other malware, is to get the malware injected into a device, a website, or an application. The bot-herders or the attacker finds a vulnerability and then exploits it in order to attach or inject the malicious piece of code.
The next phase depends on the user/target, as they need to download and execute the malicious code on their PC. This is why the attackers normally attach bots to legitimate software, and the bot is deployed just like that.
At this point, the device has been compromised and the bot has been planted. Now, the attacker waits until sufficient devices have been compromised and a large-scale botnet has been created.
When the attacker is ready, they will initiate a targeted attack from all available botnets and perform their attack. During the attack, most zombie computer users do not even realize that their computer is being used for an attack.
When the desired attack is carried out and completed, the botnets go dormant again and are prepped for their next task again. This may include updating them to perform a different kind of attack.
What are botnets used for?
Botnets can be used for different purposes, and all of them are for malicious intents. Here is a list of attack types for which botnets can be used:
-
Spam emails
Botnets are beneficial in sending out spam emails in bulk. These often include malware that infects the recipient’s device. Often, these emails include more bots to recruit more devices into their malicious network.
-
DDoS attacks
Millions of bots simultaneously send requests to the same device, overwhelming its traffic, and rendering it incapable of performing its normal functions. These attacks can be carried out to disrupt services, serve as a distraction while the actual attack is taking place, or disable certain services to make way for another breach.
-
Financial and informative breach
Bots are used in the theft of sensitive data and other financial information such as credit card info, and direct theft of funds.
-
Targeted intrusions
These are smaller sets of bots that are designed to target specific services or servers so that more botnets can be used to penetrate further into the network. These types of attacks are the most dangerous of all botnet attacks as the bot-herders normally target the most high-value assets within an organization.
-
Cryptojacking
Some bots are used to utilize the resources of the victim’s device in order to mine cryptocurrency.
-
Brute-force attacks
Bots are used to repeat the action of inserting or guessing a username and password in an attempt to log into a user account without their authorization.
How to protect against botnet attacks
Here are a few things you can do to protect your assets from botnet attacks:
- Keep OS and software updated
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Reduce attack surface
- Monitor network traffic
- Use honeypots
- Increase network bandwidth
- Employ a Content Delivery Network (CDN)
Logic bombs
Logic bombs may or may not be considered malware – there is a fine line. However, most logic bombs are either worms or viruses.
What makes a logic bomb unique is its ability to execute the payload or the malicious piece of code, when certain conditions are met. For example, an attacker might configure a logic bomb to go off on a specific date at a specific time.
When such conditions are combined with a malicious piece of code, it is considered a logic bomb. An attacker may also set different kinds of conditions. For example, a network engineer might deploy a logic bomb that would disrupt the network so that they can return to the same organization later, fix the issue, and get another payday.
Are logic bombs more dangerous than other malware?
Deciding whether regular malware is more dangerous than a logic bomb entirely depends on the severity of both of them. Some may consider logic bombs to be more dangerous because not only do they lie dormant and undetected on the devices, but they are also usually configured to go off when you least expect them.
For example, an attacker may program a logic bomb to go off as soon as it detects that the firewall is off. Or, a logic bomb may go off when no security professionals are logged into the system
That said, worm logic worms can be considered the deadliest kind of malware as they can propagate through the entire network without human activity.
How logic bombs work
Log bombs need to be planted on a device. They can be planted using phishing emails, or other means, like backdoors and trojans. Once planted, if they are a virus, they can attach themselves with a file and propagate through the network if shared. If they are a worm, then they can propagate through the network on their own.
Once it reaches the desired device, it plants itself and then waits for the conditions to be met. Once the defined conditions are satisfied, the logic bomb will unleash the devastating payload and begin its attack.
How to protect against logic bombs
Here are a few things you can do to protect your assets from logic bombs:
- Beware of phishing/social engineering schemes
- Use secure authentication methods
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Use encryption
- Avoid public networks
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Enable/use firewalls
- Close listening ports
- Regularly backup data
- Reduce attack surface
- Enable controlled folder access
- Use adblockers
- Purchase ad-free devices
- Employ a Content Delivery Network (CDN)
- Use Access Control Lists (ACLs)
Fileless malware
Fileless malware does not need files and other tangible data to execute its malicious payload. Fileless malware corrupts and uses legitimate software to infiltrate systems and then carry out its evil activities.
Typical malware is based on files and code. This is not true for fileless malware. Malware with files is easy to detect and is almost instantly quarantined by antimalware software. However, fileless malware is much more difficult to detect, making it one of the most dangerous types of malware.
Similar to other malware, fileless malware can be used to perform a bunch of different tasks, such as stealing information, planting another malware, creating a back door, etc. However, one major difference of fileless malware is that it is executed within the device’s memory, and never touches the storage hard drive.
This is what makes the fileless malware undetectable and dangerous. Moreover, this sort of attack is relatively new and was first carried out in 2017.
How fileless malware attacks work
Like all other malware, fileless malware first needs to penetrate into the target system. For this, the attackers usually find and exploit vulnerabilities in reputed software before injecting the malicious code within them, like Windows PowerShell. These are the software that is whitelisted and usually allowed to run within organizations.
When the software is downloaded and installed on the target computer, so is the fileless malware. It then goes straight into the system’s volatile memory, undetected, and performs its task in silence.
Such malware can also propagate from one system to another within the network.
Types of fileless malware attacks
There are different kinds of fileless malware attacks mostly based on their approach toward the attack. Here are the different types of fileless malware attacks:
-
Exploit kits
Exploit kits are a set of exploits designed specifically to penetrate operating systems or applications and programs. This is one way for the attackers to get their malicious piece of code into your PC. These then travel into the memory where they are executed without being detected by the in-place security software.
-
Registry-resident malware
Such fileless malware injects itself into the operating system’s registry files and changes the values. These are usually injected by dropper programs, which are the legitimate apps and programs that have been exploited, and they write the code for the Windows registry. This then allows the malware to remain undetected, executing itself and regularly making changes to the registry.
-
Memory-only malware
As the name implies, these fileless malware remain and run within the system’s memory, allowing them to go undetected as long as possible.
-
Fileless ransomware
A ransomware attack is when the files on the computer and encrypted and locked away by malicious software, and the attackers demand a ransom amount to unlock the data. with advancing technology, instead of using malicious software, attackers are now using fileless attacks to execute ransomware attacks.
-
Stolen credentials
An attacker may steal legitimate user credentials and carry out a fileless attack from that account so that they can go undetected for prolonged periods. Once they have penetrated the network, they can use trusted and native tools, like PowerShell and Windows Management Instrumentation (WMI) to carry out the fileless attack.
Detecting fileless attacks
As mentioned earlier, fileless attacks are sophisticated enough to go undetected by standard antimalware and other security tools. Therefore, a different approach might be needed. Here are two ways you can identify when a fileless attack is underway:
-
Look out for attack indicators rather than indicators of compromise
This statement means that you look for abnormal activity on your computer instead of malicious files and malware. This is called looking for indicators of attack, rather than looking for the indicators of a system compromise.
This is a realistic and efficient approach toward detecting fileless attacks, as they normally go undetected by even the most sophisticated security software.
-
Use managed threat-hunting
Managed threat-hunting refers to hiring a professional third party to search for and exterminate threats from your device. Since keeping a lookout and detecting fileless attacks is a rigorous and time-consuming process, it is often preferred to hire third-party security professionals to do that for you.
Of course, you cannot hire a security professional without knowing whether there is an attack in progress. Therefore, people normally hire them to monitor the activity on the device on a regular basis and report/terminate anything suspicious.
How to protect against fileless malware
Here are a few things you can do to protect your assets from fileless attacks:
- Beware of phishing/social engineering schemes
- Use secure authentication methods
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Use encryption
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Regularly backup data
- Reduce attack surface
- Enable controlled folder access
- Use adblockers
- Purchase ad-free devices
- Monitor network traffic
- Use Access Control Lists (ACLs)
Wiper malware
A wiper malware “wipes” the data on the system clean. Its purpose is to disrupt the work, cause data loss, and nothing else. Wiper attacks can cause data loss by clearing out the data tables, encrypting the data for them to never be recovered, and some other methods as well.
A wiper malware works pretty much on the same ideology as ransomware. It initially needs to gain access to a device on a network, and if it is a worm, it will propagate through the network and infect other devices without the need for human interaction.
Wiper malware was initially introduced in 2012 when the Saudi oil companies were first targeted. However, in recent times, these have been used in abundance by the Ukrainian government during the Ukraine-Russia war.
The wiper malware has always remained uncommon since it did not benefit the attacker. They neither made a profit nor any other gains. However, wipers could be used to disrupt services so the attackers can perform additional attacks while the victims are distracted.
How wiper malware works
Wiper malware and ransomware have much in common, including injection methods. The first step, like all malware, is to inject the wiper malware into a target PC. This malware can be delivered through spam emails, website infection, or through legitimate software that has been compromised.
Once the malware is delivered, it can perform any of the following malicious activities to get rid of the data:
- Overwrite existing files with blank information.
- Encrypt the files and lose the decrypting key for good.
- Corrupt the Master Boot Record (MBR) which is responsible for booting up the PC.
- Curropt the Master File Table (MFT) where every file on the device is stored within the memory, making them inaccessible.
How to protect against wiper attacks
Here are a few things you can do to protect your assets from wiper attacks:
- Beware of phishing/social engineering schemes
- Keep OS and software updated
- Use non-administrative/standard account
- Use trusted antimalware
- Perform regular scans
- Avoid clicking malicious links and websites
- Avoid clicking popups
- Use encryption
- Avoid public networks
- Adjust browser security settings
- Enable SmartScreen
- Enable Tamper Protection
- Do not connect untrusted storage devices
- Change User Account Control (UAC) settings
- Increase internet security level
- Enable/use firewalls
- Close listening ports
- Regularly backup data
- Reduce attack surface
- Enable controlled folder access
- Use adblockers
- Purchase ad-free devices
- Use honeypots
Takeaway
There are many different types of cyberattacks; one of them is through malware. Furthermore, there are different kinds of malware as well. Some are defined by the action of the malicious payload, while others are defined by how the malware propagates.
On this page, you find details on all the different kinds of malware and how they function.
Frequently Asked Questions (FAQs)
Is a trojan horse a virus?
A trojan is a kind of malware that is delivered by something that seems legitimate but actually contains malicious code. Therefore, if a virus is disguised as a legitimate app or program, it is a trojan virus.
Is malware and a virus the same?
While the words “virus” and “malware” are often used interchangeably, they are not the same. A virus is a type of malware, while all malware may not be a virus. A virus is a special type of malware that propagates through a network using a host, like a file. It cannot propagate on its own.
Is a virus and a worm the same?
A virus and a worm are not the same. While a virus needs a host to attach itself to and propagate, a worm does not. A worm can make its way through the network and inject the devices without a host, nor does it need user input to release the malicious payload.
Is a virus the same as a computer worm?
Even though a virus and a worm are both malware, they are not the same thing. While a virus needs human interaction to propagate, a computer worm does not. Moreover, a virus also needs to attach itself to a host to move about, a worm is independent and does not require a host.