Key Points
- Zero-day vulnerabilities are discovered before the manufacturer knows about it, and is actively being exploited, and they have 0 days to fix it.
- Zero-day attack is the process of carrying out nefarious tasks, zero-day exploit is the technique/method used to take advantage of the vulnerability, and zero-day vulnerability is the unknown loophole in a software’s code that is being exploited.
Zero-day attacks are something every person may have heard at one time or another. Also referred to as “0-day” attacks, these are a type of cyberattack that is dependent upon a software vulnerability. When an unintentional vulnerability exists within the software, attackers take advantage of it and exploit it for nefarious gains.
Zero-day exploits have been occurring for some decades now, and are still popular amongst hackers. This is because zero-day vulnerabilities still exist in today’s software. Whether it is an operating system, a web browser, or any other software; the chances of vulnerabilities will always be there. The only question is whether it is publically known, and if it is, has it been exploited yet or not?
This kind of attack is just as dangerous as any other cyber threat. In this post, you will learn everything there is to know about zero-day attacks and the steps you can take to make sure that your devices are as secure as possible.
This page covers
What is a Zero-day attack
A zero-day attack refers to a cyberattack that occurs because an unintentional vulnerability has been exploited by attackers.
This usually happens once the vulnerability has been publicly disclosed by an individual, or has been public knowledge and a script already exists to exploit it. Before this, the manufacturer of the software wouldn’t possibly know about the vulnerability. However, once it has been made public, the attackers instantly develop specialized malware to exploit the vulnerability, if it doesn’t already exist.
Such an attack is called a “zero-day attack” because the manufacturer has 0 number of days before they can fix it. This is usually after the vulnerability is already being actively exploited, and the manufacturer has zero days to fix it. Normally, the manufacturers get right on releasing a hotfix or a security patch and fixing the vulnerability, but it is already too late.
Zero-day attacks vs. exploit vs. vulnerability
Sometimes, the terms “zero-day attack,” “zero-day vulnerability,” and “zero-day exploit” are used interchangeably. However, there are minor differences between the terms:
- Zero-day vulnerability: It is a recently discovered and unintentional security flaw within software that the manufacturer is unaware of, or has not been able to patch yet.
- Zero-day exploit: An exploit is a technique the attackers use to take advantage of the discovered vulnerability.
- Zero-day attack: The attack is the process of exploiting a zero-day vulnerability that results in damages, in either data theft, downtime, or financial gains.
Although the 3 terms mean different things, they all refer to the same just-discovered vulnerability. The attackers react fast in fabricating a specific exploit for the vulnerability, which is tailor-made, and are usually successful in bypassing the in-place security checks because of the vulnerability.
How zero-day attacks work
A vulnerability can exist in any kind of software, may it be an operating system, a Microsoft Store application, a browser extension, or a third-party software. These vulnerabilities are normally unknown to the developers as well, otherwise, they would patch it before releasing the software or rolling out an update.
A vulnerability within software can be discovered by individuals, or the hacking organizations who devote their lives to performing attacks in exchange for financial benefits. Once discovered, it may or may not become public knowledge. Usually, the vulnerability is announced via proper channels (and often privately) so that the developers can take the necessary action before it is exploited.
However, if a vulnerability is discovered by hackers, or is being actively exploited already, it is less likely to become public knowledge, so they have ample time to exploit it before it can be patched up. Sometimes, it can take days, and even months before the developers become aware of a vulnerability in their software. In such instances, when the vulnerability does become public knowledge, they see that an exploit already exists, and hence is a zero-day vulnerability.
That said, the attackers still need access to the systems where the software and the vulnerability exist so that it can be exploited. For that, the attackers reach out to the users via phishing scams and other baiting techniques. For those purposes, the attackers may send out malicious emails with either malware which the user accidentally downloads, or links to other malicious websites.
When this approach is taken, the users are also at risk. With these attacks, the attackers could not only exploit the zero-day vulnerability, but could also perform other attacks, like planting spyware, rootkits, or worms. That said, the executed malware also includes code that will exploit the vulnerability, creating access for the attackers.
This is how a zero-day vulnerability creates an opportunity for the attackers to benefit before the developers can roll out a security update for the software.
In an alternate scenario, a zero-day vulnerability could be patched before anyone had a chance to exploit it. If the vulnerability is patched and no longer exists, it can no longer be referred to as a zero-day vulnerability.
Which software is vulnerable to zero-day attacks?
There is no defined category for the type of software that may be prone to zero-day exploits. It is all about whether a vulnerability exists, and if it does, whether or not it has been discovered yet.
A loophole in software may exist that nobody knows about. For example, a developer may create software from scratch, and then publish it, without testing it for security vulnerabilities. In this scenario, neither the end-user nor the developer would be aware of the vulnerability. Note that the software could be of any type, size, and purpose.
Here are a few examples of software that could be exploited with zero-day attacks:
- Operating systems
- Web browsers
- Office applications
- Open-source components
- Hardware and firmware
- Internet of Things (IoT)
The list is not only limited to these software categories. As long as it is software, chances for zero-day vulnerabilities exist.
Victims of zero-day attacks
Like software, there is no defined target audience for the people who may fall victim to zero-day attacks. Moreover, the purpose of the attack could range from disrupting operations to creating backdoors for delayed access.
Here is a list of potential victims of zero-day exploits:
- Individual/home users with vulnerable systems and software
- Users with access to sensitive information
- Business and organizations; for financial information or operation disruption
- Devices connected to the Internet of Things
- Devices with firmware
- Government organizations
- Individuals or employees using a very specific software
While some zero-attacks are targeted toward specific audiences, other attacks are usually carried out against users with vulnerable software, like a specific operating system or an app.
Examples of zero-day attacks
As mentioned earlier, zero-day attacks have been around for decades. There is a vast history of notorious zero-day exploits that ought to be enough for us to learn our lesson and keep our devices safe. Here are a few infamous examples:
-
Zoom, 2020
In 2020, some hackers infiltrated devices on Windows 7 with a vulnerability discovered in the Zoom online meeting platform. They could remotely access the vulnerable computer, and if the user account had administrative privileges, the attacker could gain complete access to the system and the files.
-
Windows OS, 2019
The attackers targeted government organizations in Western Europe that were using a Windows operating system and performed local escalation of privileges. The attackers were able to run an arbitrary code, install applications, and view and change the data on compromised applications.
-
Stuxnet
Stuxnet was a computer worm that was discovered in 2010, but actually dated back to 2005. It was a worm that affected manufacturing computers that ran Programmable Logic Controller (PLC) software.
The initial target of this attack was Iran’s uranium enrichment plants to disrupt the country’s nuclear program. The worm infected the PLCs through vulnerabilities in the Siemens Step7 software, causing the PLCs to carry out unexpected commands on assembly-line machinery.
-
Microsoft Word, 2022 (Follina)
A zero-day vulnerability was actively exploited in 2022 when the attackers were able to perform Remote Code Execution on the victim’s computer (CVE-2022-30190). The attackers only needed the victim to download and run a simple Word (.DOC) file, and the rest happened in the background without the user knowing.
This attack granted the users full access and code execution via the command line. The code name for this exploit was “Follina.”
There are many notorious zero-day attacks in our history, and these are only a few examples that depict just how dangerous such exploits could be.
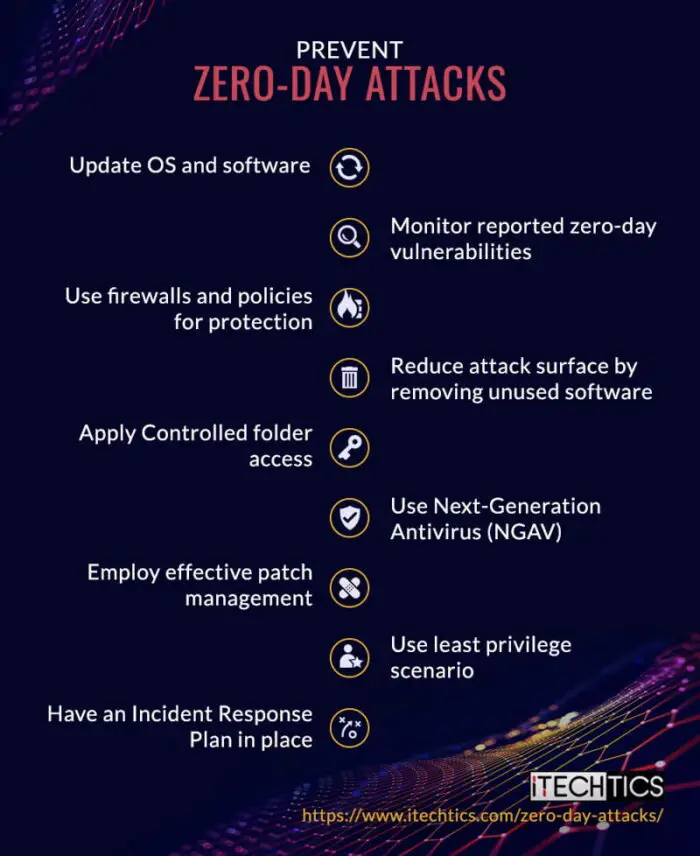
How to prevent zero-day attacks
Zero-day attacks can originate from any source, and through any software with a vulnerability. Therefore, preventing zero-day exploits from executing on your computer is a sophisticated task. You must always be on your toes while using the computer so no malware can find its way.
Here are some best practices you can adopt to prevent zero-day attacks:
-
Keep the operating system updated
As we have learned so far, zero-day exploits are executed on vulnerabilities that have recently been discovered. Vulnerabilities could also be exploited if they are specific to operating systems, like the Elevation of Privilege.
Keeping your operating systems updated ensures that the latest security updates have been applied and any identified vulnerabilities have been patched.
Follow these paths in the respective operating system to check for pending OS updates. Install them if available.
- Windows: Settings >> Windows Update >> check for updates
- macOS: Apple menu >> System Settings >> System Settings >> General >> Software Update
- Android: Settings >> Software update >> Download and install
- iOS: Settings >> General >> Software update
-
Install the latest software updates
Similar to operating systems, software updates are just as critical for patches both known and unknown vulnerabilities.
Manufacturers roll out hotfixes and regular security updates which include the latest available definitions for keeping the software and the devices secure. You must install these updates as they are published.
However, as a point of caution, we do suggest that you go over the release notes for the updates to make sure that the update does not introduce new vulnerabilities or issues rather than fixing the existing ones.
-
Monitor reported vulnerabilities
Black hat hackers, which are the hackers that exploit vulnerabilities for nefarious reasons, are not the only ones finding loopholes. White and grey hat hackers are also searching for vulnerabilities across different software, and when discovered, report them to the manufacturer via proper channels.
Once reported, the vulnerabilities become public knowledge and are posted on various platforms. We recommend that you keep an eye out on such platforms and look for any vulnerabilities in software that you or your organization uses. this will help you keep a step ahead in protecting your devices. You can find information on reported vulnerabilities on www.talosintelligence.com; a platform by CISCO.
If a vulnerability is critical and you fear that it could be exploited, you can proactively take the necessary actions to prevent that.
-
Use firewalls
The use of firewalls, whether hardware-based or software-based, is always recommended. However, the sophistication level of the firewall is totally dependent on your usage. If you are a regular home user and use your system for basic tasks, then the built-in Windows Security firewall ought to be sufficient. However, if you are an IT-based organization, then you may want to opt for Next Generation Firewalls.
There are different types of firewalls available; some even include Intrusion Detection and Prevention Systems. Additionally, you should also use Web Application Firewalls to protect web-based applications.
Firewalls have different preventive systems integrated that can p[protect you against zero-day exploits, including antimalware, packet inspection, intrusion prevention, and excrypted traffic inspection. Additionally, you can configure policies on firewalls to specifically protect the internet network from zero-day attacks which have been discovered by monitoring tools.
-
Reduce attack surface
The attackers use software to exploit existing vulnerabilities to perform zero-day attacks. The less software you have on your system, the fewer the chances of zero-day attacks. Hence, keeping apps and software that are no longer in use exposes your system to such exploits.
Any piece of software should be removed from the computer if it is no longer being used. If it is not being used, then it is likely not being updated either. This inflicts a greater risk of exposure to zero-day attacks.
Another method for reducing the attack surface is closing the points of entry for unauthorized users into your network. This involves closing listening ports, placing stricter policies, using Access Control Lists, etc.
-
Enable Controlled Folder Access
Controlled Folder Access is a Windows feature that limits access to critical system folders. Although it exists to prevent ransomware attacks and other threats, it can also prevent zero-day attacks that need to access the system files for exploitation.
For example, certain attacks implement the Elevation of Privilege technique to gain complete control of the system. However, if the access of the malicious piece of code is automatically blocked from accessing the system files, the exploit might not work.
Here are the steps to enable Controlled Folder Access on Windows:
-
Press the Windows Key + I to open the Settings app.
-
Go to the following:
Privacy and Security >> Windows Security >> Virus and threat protection
-
Click “Manage settings” under “Virus and threat protection settings.”
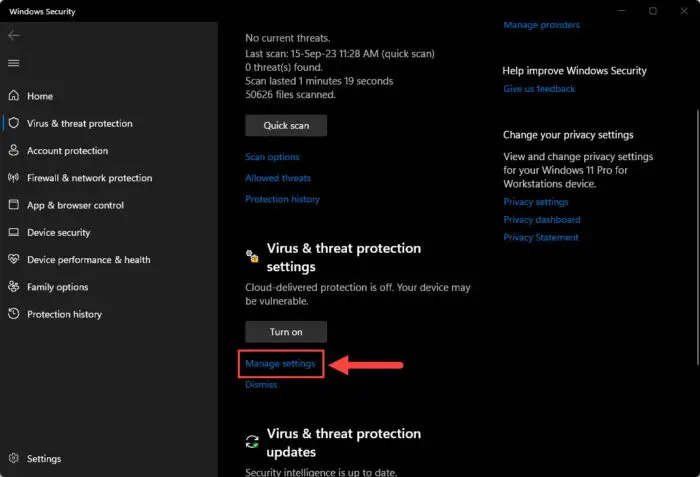
Manage virus and threat protection settings -
Click “Manage Controlled folder access.”
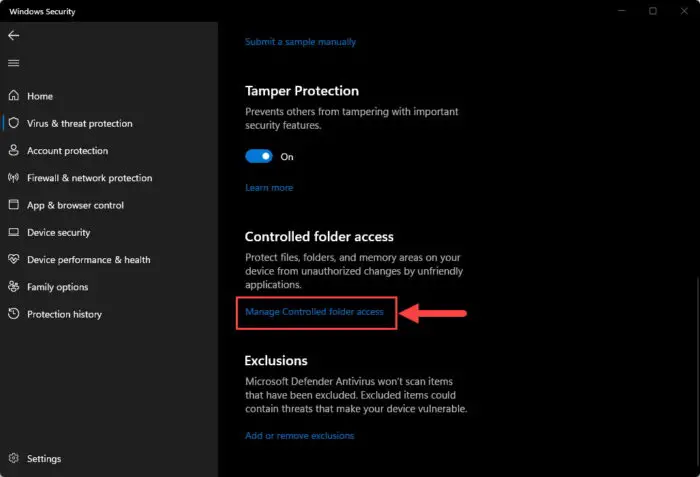
Manage Controlled folder access -
Toggle the slider below Controlled folder access into the On position.
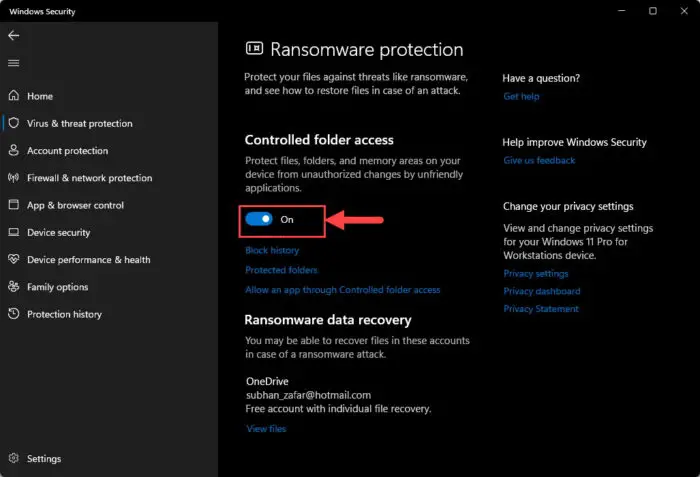
Enable Controlled Folder Access
-
-
Use Next-Generation Antivirus (NGAV)
Like Next Generation Firewalls, Next Generation Antiviruses are also advanced versions of the regular antivirus software.
Sometimes, the regular antimalware isn’t enough to protect against zero-day attacks, since their definitions have not been updated yet. However, Next-Generation Antimwalre performs signature-based detection, and can thus block malicious pieces of code and cyberattacks without the need for precise definitions.
To detect that a system is infected with malware, Next Generation Antivirus solutions use threat intelligence and behavioral analytics to create a behavioral baseline for a system. It also uses suspicious anomalous behavior and machine learning code analysis to identify that a system is infected.
When such malware is found, NGAV can stop harmful processes and prevent the attack from affecting additional endpoints.
-
Implement effective patch management
Patch management solutions exist so that you can source software updates directly from the vendors and deploy them to your systems throughout the organization.
Note that the updates are made available by the manufacturer after the vulnerability is likely exploited (in case of a zero-day attack). Therefore, patch management systems may not exactly prevent zero-day attacks, but will reduce the potential impact time significantly.
-
Practice the least privilege scenario
The least privilege scenario is where every user on the domain has the minimum privileges needed to perform their tasks. For example, if a user can get their work done while having a standard user account, then do not grant their user accounts administrative rights – since they do not need them.
A standard user account in Windows has limited privileges to perform tasks. For example, they cannot change the properties of other user accounts, install computer-wide software, etc. On the other hand, administrative accounts have complete control over the computer, as well as the other user accounts on it.
If an account is compromised, and it turns out that the account has administrative privileges, then the attacker who has control of the user account would have complete rights to perform nefarious tasks across the PC, and maybe even move laterally through the network and infect other devices.
-
Have an Incident Response Plan in place
An Incident Response Plan is exactly what it sounds like. It is a set of rules, policies, norms, and actions to follow, in a specific order, that you need to adopt in case there is a breach. Although this approach does not precisely prevent zero-day attacks, it will most certainly reduce the impact of an attack.
The SANS Institute, which is America’s reputed cybersecurity company, has published the following 6-stage incident response plan that you can follow to create your own:
- Preparation: Identify the most important assets and calculate the risk if they were to be compromised. There will be the assets the security team will focus on going forward. Prepare documentation that highlights the roles, responsibilities, and processes of each asset.
- Identification: This portion covers how to detect zero-day attacks; the exact processes to follow, and the tools involved. It also discusses how to validate that a zero-day attack is occurring within a timeframe.
- Containment: The immediate action that needs to be taken for damage control and to reduce the impact of the attack.
- Eradication: Identify the root cause of the attack and ensure steps are taken to prevent similar attacks.
- Recovery: Begin the recovery steps to bring the assets back online and functional, while making sure that all traces of the exploit have been dealt with. This section should also cover the duration of critical monitoring to confirm that the operations are back to normal.
- Lessons learned: Discuss the aftermath of the attack and provide feedback on how the processes can be further improved so that you are better prepared for future attacks.
Takeaway
As long as there are updates being released for software, zero-day vulnerabilities will continue to exist. While some companies focus on including more security patches, some simply focus on providing new and improved functionality to their customers. In the latter case, they often forget to include the latest security definitions, leaving their software products vulnerable.
Therefore, simply keeping your software up to date may not be enough to prevent zero-day attacks. That is why you must also use advanced detection and prevention tools, like Next-Generation Antiviruses, to protect your systems, assets, and the organization from zero-day attacks.