Key Points
- XSS attack is when a website or web app vulnerability is exploited to inject malicious content onto end-user’s web browsers.
- There are three types of XSS attacks: Stored (persistent) XSS, Reflected (non-persistent) XSS, and DOM-based XSS.
- Preventive measures for XSS attacks need to be performed on both the website and the end-user device.
Cyberattacks are increasing every day. Not only are they increasing in number, but the types of cyberattacks are also becoming more sophisticated.
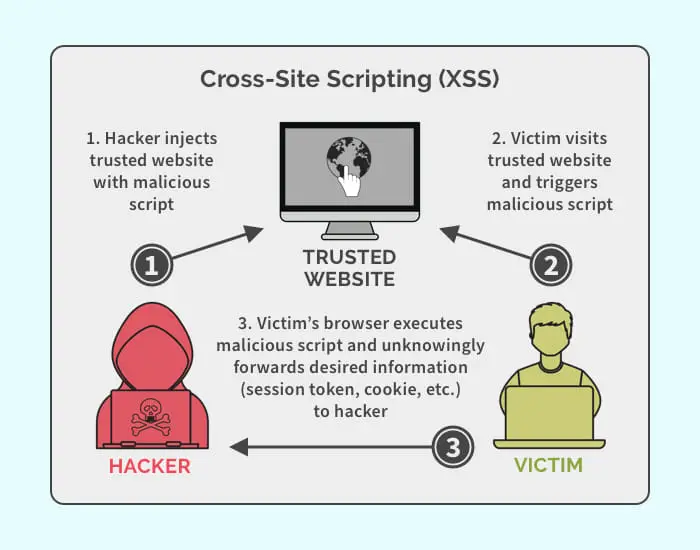
One such attack is the Cross-Site Scripting (XSS) cyberattack. In this attack, a vulnerable website, web page, or web application is compromised by the attacker to inject malicious code into the end user’s web browser. This attack can be carried out to gain unauthorized access to user data who visit the website, deface the website, or simply gain access to everything within the website to which the users have access.
XSS attacks can be complex and can be planted without user interaction. This means that your session can be hijacked simply by visiting a compromised website. Note that the owner of the website may or may not be aware that their website has been injected with malware, and therefore, preventing XSS attacks is just as important for the website owners as it is for the end users visiting the compromised web pages.
Here, we talk about everything there is to know about Cross-Site Scripting, how it works, and what you can do to prevent it from infiltrating your browser (in the case of end users), or your website (in case you are a website owner).
This page covers
What is Cross-Site Scripting?
All websites adhere to the Same Origin Policy (SOP). Under this policy, all scripts that can be executed on a website must originate from the same source. This policy is enforced to prevent scripts from one website from being executed in another. However, the websites that haven’t enforced this policy are vulnerable to XSS attacks.
A Cross-Site Scripting attack is very much similar to an SQL injection attack. It takes advantage of browsers’ inability to discern between safe and dangerous markup. Thus, they execute whatever markup text they receive and provide it to end users upon request.
If a web page or web application uses user input that is unsanitized before executing it, it is susceptible to XSS attacks.
XSS attacks can be carried out in CSS, VBScript, ActiveX, Flash, and JavaScript. However, JavaSCript is the most common and the most favored XSS attack platform since it is fundamental to almost all web browsers.
What is Cross-Site Scripting used for?
XSS attacks can be carried out for different purposes. While the majority of the attacks are carried out to gain user login credentials and access information that only the user can see, other XSS attacks can be carried out for simply defacing the web page or the web application of a rival.
At other times, an XSS attack can also be carried out for financial gain or disruption, but this mostly depends on what kind of web application it is.
Here are the possible reasons for which an XSS attack can be carried out:
- To impersonate a user on the website.
- Capture the user’s login credentials.
- Carry out tasks that only a user can perform.
- Access information that only a user can.
- Deface a web page or a web app.
- Steal financial information for personal benefits.
- Gain access to Personal Identity Information (PII) or other sensitive data.
Types of Cross-Site Scripting
Now that we understand what Cross-Site Scripting is, it is also important to know that it has different types. These types are differentiated depending on how the XSS attack occurs. These are the 3 main types of XSS attacks:
- Stored (persistent) XSS attack
- Reflected (non-persistent) XSS attack
- DOM-based XSS attack
Stored (persistent) XSS attack
Stored, or persistent XSS attacks are those where the malicious code is injected into the server or the database by an attacker. The attacker injects their code into the server of a vulnerable website or web app, which is then transferred onto the user’s (victim’s) PC when they generate a request.
In this type of attack, the attacker usually exploits and injects their malicious code in places accessible by the users, such as comment boxes. When a user visits or interacts with the compromised object, the malicious code is transferred to the target PC where it is then executed.
Reflected (non-persistent) XSS attack
Reflected XSS attacks are called so because of their reflective behavior. This type of XSS attack is reflected off of a legitimate web server and includes the whole or part of the original user input. This may include error messages, search results, etc. Here, the user is tricked into clicking a malicious link, which then triggers the malicious code to be delivered to the original web page, and then travels onto the target’s PC.
The malicious is then executed in the web browser automatically since it came from a trusted source.
Note that reflective XSS attacks are normally delivered via a different route than the original web page that the victim visits. These can be delivered via a malicious link on the error page or phishing emails.
DOM-based XSS attack
In such XSS attacks, the attacker modifies the Document Object Model (DOM). These attacks are very similar to reflected XSS attacks because it is delivered through phishing emails and malicious links. However, the difference lies in where the malicious script is executed.
Instead of including the payload in the HTTP response of a trusted website, the attack is solely carried out in the web browser by modifying the DOM. This can usually be done when the web app contains client-side JavaScript.
How Cross-Site Scripting works
We have learned that XS attacks can be of different types, depending on where the code the executed and where it is stored. However, their functioning pattern is mostly the same. These are the steps for executing a Cross-Site Scripting attack:
-
Code creation
Every XSS attack is tailored to infiltrate a special vulnerability on a web page or a website and exploit it. Therefore, after discovering a vulnerability, the attacker creates a code to exploit it.
-
Injecting the code/script
Once the code is prepared, the attacker then needs to inject and plant it into the website. It could be injected into the server, or placed in an interactive box so it can travel to the target’s browser when a request is generated.
-
Transferring the malicious code
The next phase involves moving the code onto the user’s browser so that it can be executed. This happens when the target user clicks on a malicious link, or interacts with a button or dialog box which transfers the malicious script onto the target browser, and then automatically executes it.
-
Data theft
This step is not always true, as it depends on the script created by the attacker. The XSS attack may steal your data, like cookies, tokens, and other sensitive information.
-
Results
This step is when the code has been successfully executed and the attacker finally gets what they intended. This could be defacing a website, stealing the user’s data, or logging into the website as a legitimate user to view information available to the users.
How to prevent Cross-Site Scripting attacks
As mentioned at the beginning of the article, Cross-Site Scripting can inflict harm to both a website and the end users. Therefore, both of the involved parties need to protect their assets from XSS attacks as much as they can.
Keep websites/web apps safe from XSS attacks
Test for XSS vulnerabilities
The first thing a website owner should do is get their website tested for XSS vulnerabilities. These are the vulnerabilities that are likely to be exploited by attackers to gain access to your website and plant malicious code.
A website can be checked for vulnerabilities using several methods. However, the Open Web Application Security Project (OWASP) recommends that you use the Black-box Testing techniques to test for XSS vulnerabilities. Note that when performing these tests, the tester must assume that the browser itself won’t prevent the attacks.
Variable Validation
Variable validation is a method for figuring out whether an input meets your intended criteria. Making sure that only safe and well-organized data enters your application will help to reduce the likelihood of malicious code infiltration.
To make sure that an email address resembles one that is anticipated by a user, utilize filters or regular expressions. Avoid sensitive procedures, and if it deviates from the expected format, show an alert to the user.
Output encoding
Output encoding is another defense against XSS attacks. Before presenting dynamic material in HTML on your website (like comments), it must be correctly encoded. To prevent the browser from interpreting special characters as code, special characters must be encoded into other harmless equivalents.
By encoding, script tags in user contributions are made sure that they display as regular text rather than running as scripts. To aid developers with secure encoding, OWASP provides a “cheat sheet” that you can benefit from.
HTML sanitization
HTML sanitization is the process of eliminating any scripts or other elements from user-generated HTML that might be dangerous for the website. HTML sanitization serves as a safety net, eliminating or neutralizing any potential threats before user input is shown on your website.
For example, HTML sanitization ensures that only safe content is shown to readers by filtering out any harmful components or characteristics from a blog post that contains user-generated HTML code. By doing this, you keep your website secure and defend visitors from potentially harmful scripts.
For HTML sanitization in web applications, it’s crucial to utilize reliable, well-maintained libraries. OWASP recommends DOMPurify as a practical solution in the battle against XSS attacks.
Cookies are used to track online movement and store user preferences. Setting attributes changes how JavaScript and web browsers can interact with cookies.
Cookie attributes make an effort to reduce the effect of an XSS attack, but they don’t stop malicious material from being executed or deal with the vulnerability’s underlying problem.
Content security policy (allowlist)
An allowlist, or a whitelist is a cybersecurity defense strategy to allow only certain IP addresses, domain names, etc. to be able to access certain data. In the case of a website, the allowlist becomes a list of things that is loaded. Anything except those will not be loaded onto the web page or the web application; like a malicious script.
These are the methods that you can use to secure your web application or website from XSS attacks. Note that there are also other strategies and not only limited to these basic tasks.
Prevent XSS attacks from executing in browsers
Increase browser security
By default, most web browsers have moderate security policies in place and not the strictest. If you do not increase your browser’s security, you are more likely to be affected by XSS attacks.
If you didn’t know, most modern web browsers have built-in security settings that allow you to harden it. This way, you can prevent cookies from tracking your online activity, automatically block popups, and reduce the attack surface for a malware attack. Some browsers are even capable of blocking malicious files and content by identifying that they are not trusted, or are unsigned.
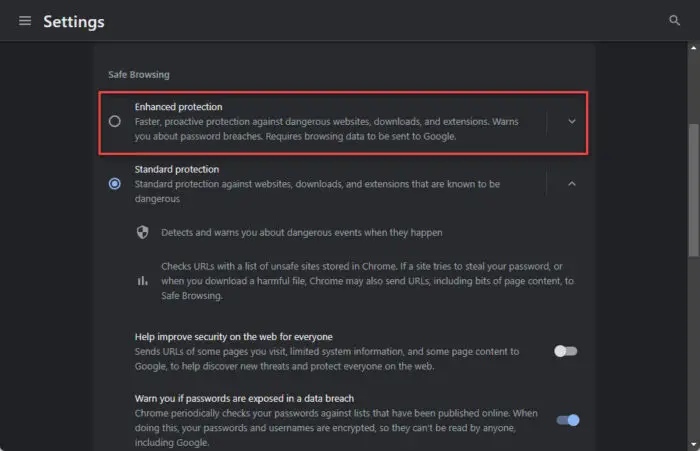
Normally, the default security settings are mild. You can manually change these settings in the browser’s settings. For example, in Google Chrome, you can go to Settings >> Privacy and security >> Security, and select “Enhanced protection” to increase your web security to the maximum.
Enable SmartScreen
If you are using Microsoft Edge as your web browser, then you should enable SmartScreen. SmartScreen provides on-the-go web security by scanning websites and downloading malicious files.
SmartScreen protects against phishing and malicious websites by automatically detecting and blocking malicious content. It uses a list of reported malicious software sites and programs known to be unsafe to crosscheck whether you have accidentally downloaded one. It also applies the same logic to files.
Use the following steps to enable SmartScreen in Microsoft Edge:
-
Open Microsoft Edge.
-
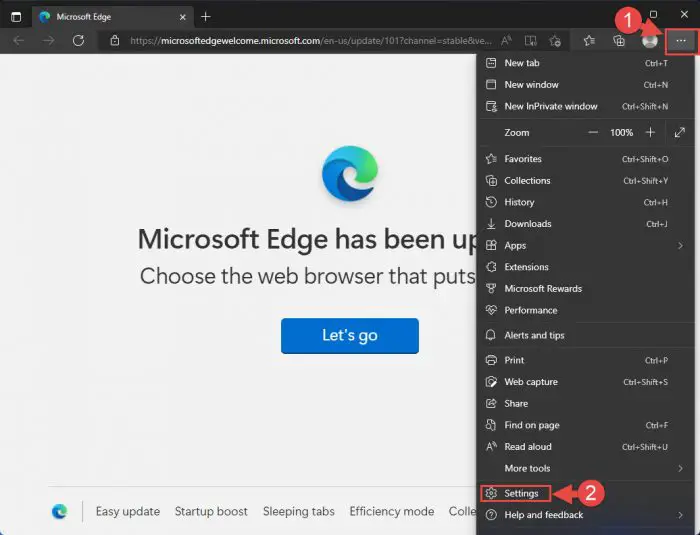
Click on the 3 dots in the top-right corner and then click Settings.
Open Edge settings -
Click “Privacy, search, and services” on the left.
-
Scroll down to the Security section and toggle the slider in front of “Microsoft Defender SmartScreen” into the On position.
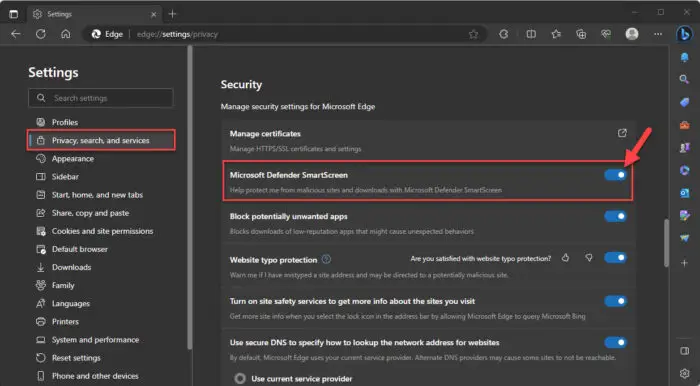
Enable Microsoft Defender SmartScreen
Increase internet security level
The Windows operating system also has a zone-based security level. This means that you can change the security level of the internet.
By default, this setting is “Medium-high,” which allows you to download potentially unsafe content with only a warning, and is appropriate for most websites. However, changing it to “High” will ensure maximum safeguard and is appropriate for even harmful content.
To change the internet security level, use these steps:
-
Press the Windows Key + R to open the Run Command box.
-
Type in “inetcpl.cpl” and press Enter to open the Internet Properties applet.
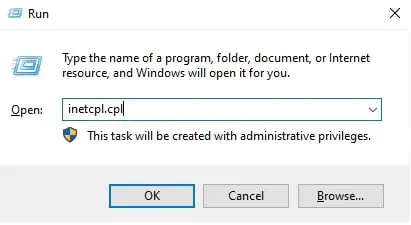
Open the Internet Properties applet -
Switch to the Security tab.
-
Select “Internet.”
-
In the “Security level for this zone” section, drag the slider to the top position.
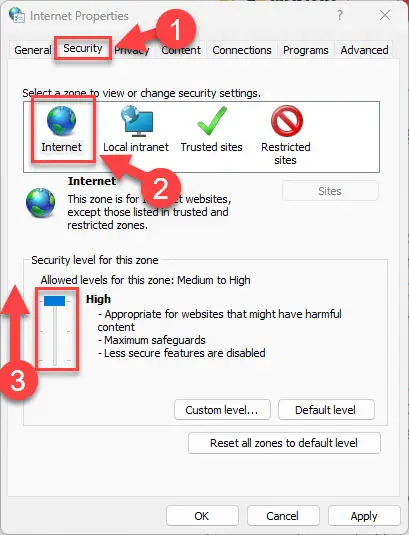
Increase internet security settings -
Now click “Apply” and “Ok” for the changes to take effect.
Beware of spam/phishing emails
Phishing is a method for attackers to obtain your personal or digital information. For example, they might send you links to malicious websites that pretend to be legitimate, so that you can enter your correct login details, which will then be available to the attackers.
In the case of XSS attacks, phishing emails can be sent to you with malicious links that redirect you to websites that will initiate the XSS attack, like in the case of reflected XSS attacks.
Ending words
Cross-Site Scripting can be one of the most dangerous types of cyberattacks today. It can not only steal sensitive information but can also use it to perform other malicious activities. Moreover, XSS attacks are used to spread malicious content and scripts. This makes them excellent tools for spreading other worms and viruses.
That said, regardless if you are an end user or a website/web application owner, it is important for you to protect your assets from XSS attacks. Ensuring maximum security may improve your chances against cyberattacks, but it still won’t mitigate them completely.