Key Points
- SQL injection attack occurs when an attacker tricks a web application into running malicious code by injecting SQL commands into a user input field.
- The best approach toward protecting your web-based app from SQL injection attacks is by sanitizing all input so that the time filters are run, and using Web Application Firewalls (WAF).
SQL injection also known as “SQLi,” is one of the most dreaded cyberattacks by web developers, as they are usually the victims. An SQL injection attack requires developers to code in such a way that it is both secure and can differentiate between malicious and regular user input.
The Structured Query Language (SQL) is a standard programming language used to develop backend database servers. It creates a relational database where the data is stored in tabular form. SQL uses a query-based input to perform tasks, such as fetching information, modifying it, or deleting it from the table.
In an SQL injection attack, even the most advanced security checks suffer in successfully detecting it. There have been instances in the past where successful SQLi attacks have created backdoors, which the attackers have been using for days before finally being detected.
If you are unfamiliar with what SQLi is, how it works, or have been a victim of it in the past and want to know how to prevent sql injection vulnerabilities, you are at the right place. In this detailed article, you will learn everything you need about malicious SQL injection attacks and how to protect your assets from them.
This page covers
What is SQL injection
SQL injection attacks only work on web pages that have SQL-based backend databases. In an SQLi, the attacker uses malicious input to change the structure of a regular input, which in turn alters the SQL table or its data.
For example, an attacker may enter manipulated SQL commands in a text box on a website which changes the meaning of the entered text. Instead of the text being considered as a simple comment, the manipulated SQL query actually alters how the website behaves.
An attacker can use this vulnerability to their advantage and gain access to information that they normally shouldn’t. An attacker can view sensitive information with SQL attacks, edit existing databases, delete content, or even perform other malicious activities such as creating backdoors, dropping malware, and deploying bots for DDoS attacks.
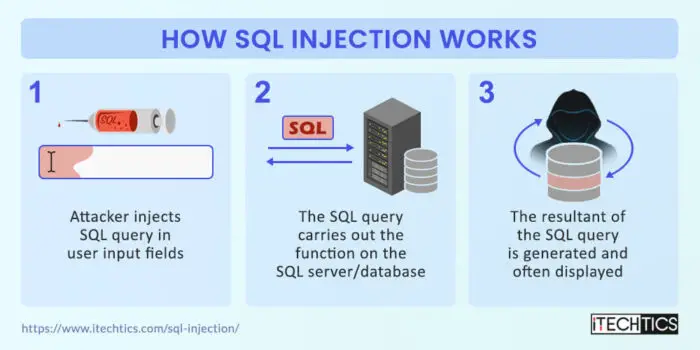
How SQL injection works
In a SQL injection attack, attackers exploit existing vulnerabilities in the SQL coding used to develop the backend of the website. If the developers fail to practice the security checks, an attacker may successfully carry out a SQLi attack.
If a web application accepts malicious input from the attacker and considers it an SQL query for the backend database, the attacker will have successfully exploited the vulnerability and continue to run additional SQL queries until they gain complete access.
An attacker deliberately injects SQL control characters into the input, so they can convert a regular input into an SQL input. They can use certain command characters like single quote (‘), double quote (“), equal (=), comment (- -), etc. to change the query structure. Alongside these characters, they can also use control keywords like DELETE, FROM, and SELECT to perform specific actions on the SQL databases.
Although most web apps are programmed not to run SQL statements from untrusted sources, the attacks can also originate from the inside, trusted sources. If an attacker is familiar with the SQL language model and detects a vulnerability, then they will probably gain access to the database by running only a handful of queries.
Why SQL injection attacks are performed
SQL injection attacks are carried out when an attacker wants to access information. The intent behind the attack could be many. For instance, an attacker may only want to access the information on the server, such as user account credentials. However, they may then want to use that information to log into the web app and see the information that is only visible to legitimate users.
Financial database servers often contain sensitive financial information, such as credit card details. An attacker may be seeking financial gain when carrying out SQLi attacks on databases with financial information. Additionally, such attacks also drastically impact the reputation of organizations and paint them untrustable in the eyes of the public.
In some cases, an SQLi attack is carried out to create backdoors. Backdoors are then used by the attackers for prolonged periods so that they can come in and out of the database servers as they please. Such attacks often go undetected and can happen in the background.
Types of SQL injection attacks
Different types of SQLi attacks are defined by how they are carried out by the attacker. Here are the main types:
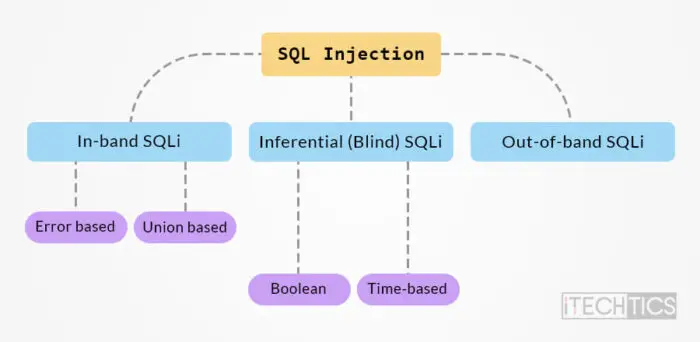
In-band SQLi
Both the attack and the result-gathering are done using the same communication channel for the attacker. One of the most prevalent kinds of SQLi attacks is the in-band SQLi due to its simplicity and effectiveness.
The in-band SQLi attackers are further divided into subcategories:
-
Error-based SQLi
The attacker causes the database to throw errors, which they then use to gather information about the structure of the database.
-
Union-based SQLi
This method takes advantage of the UNION SQL operator, which combines multiple select statements generated by the database to get a single HTTP response. The returned data is then used by the attacker for malicious purposes.
Inferential (Blind) SQLi
To gain insight into the server’s architecture and structure, the attacker delivers data payloads to the server and observes how it responds and behaves. This technique is called “blind SQLi” or Blind SQL Injection since the attacker cannot see information about the in-band attack because the data is not communicated from the website database to the attacker.
Like in-band SQLi, blind SQLi also has different types:
-
Boolean
In a boolean attack, the attacker will send a query to the database and observe whether the returned result is true or false.
Based on the returned result, the information within the HTTP response will either modify or remain unchanged, which will be a detrimental factor for the attacker on whether the response was true or false.
-
Time-based
The attacker starts by sending a query to the backend server, which makes the server wait before sending out a reply. Based on the time it takes for the server to reply, the attacker can determine whether the query returned is true or false.
Out-of-band SQLi
The attack technique is adapted when both of the above-mentioned fail. For the out-of-band SQL injection attack to work, certain features need to be enabled on the SQL server used by the web application.
When an attacker cannot use the same channel for the attack and querying information, or when the server is slow or unstable, the attacker carries out an out-of-band SQLi. These techniques rely on the capacity of the server to create DNS and HTTP requests to transfer the data to the attacker.
SQL injection examples
SQL injections have different types, which depend on the vulnerability that they want to exploit, and how the attacker can enter a custom input. Regardless, an SQL injection attack is carried out for one of the following reasons:
- Retrieving hidden data
- Subverting application logic
- Obtaining information from other tables
- Exploit blind vulnerabilities (where no data is returned to the SQL query, but vulnerabilities still exist)
To better understand how SQL injection is carried out, let us consider this example of retrieving hidden information from a table inside an SQL server.
When a user clicks on the “cars” category of a dealership, the browser will request the following URL:
https://dealership.com/products?category=carsThe app will now make an SQL query, such as the following to retrieve the cars that are in stock:
SELECT * FROM products WHERE category = 'Cars' AND released = 1The SQL query above asks the database to return the following information:
- * = all details
- products = name of the table
- Cars = where the category is Cars
- released = 1, which means true and the cars are in stock
The part of the query where “released = 1” means to show only the cars that are in stock. All cars that have been sold or are unavailable will have “released = 0”.
That said, an end user could manipulate this query by simply adding “–” (2 hyphens) at the appropriate spot, which will basically command the rest of the query. Here is an example of the manipulated SQL query that they could potentially generate:
SELECT * FROM products WHERE category = 'cars'--' AND released = 1In this example, the query after the 2 hyphens will be omitted, which means that “released = 1” will not be a part of the query, and this will result in showing all the contents of the table “products,” including those that are not in stock.
Similar to this example, the user could also manipulate the query to show the contents of all the tables, as in this example:
https://dealership.com/products?category=Cars'+OR+1=1--The resultant SQL query generated from this URL will be as follows:
SELECT * FROM products WHERE category = 'Cars' OR 1=1--' AND released = 1Since “1=1” is always true, the query will return all items where either the category is “Cars”, or 1 is equal to 1.
How to prevent SQL injections
Like most malware attacks, SQL injection cannot be prevented using conventional methods. Here is a list of prevention techniques that you can use to reduce the risk of SQL injections on your web app or website.
-
Use parameterized queries and prepared statements
The website developer should create a code so that all inputs are sanitized, and no input is treated as code. The developer should program the website to exclude command characters and control keywords, so attackers cannot manipulate the website into thinking of the input as SQL queries.
You can use prepared statements to apply filters on the inputs that automatically remove potential SQL queries before they are processed on the web server. You should also limit special characters and exclude the single and double-quote marks so the input is not mistaken as an SQL query.
-
Use Web Application Firewall (WAF)
Web Application Firewalls are usually integrated with other security solutions, making them a good suit for preventing SQLi attacks. Although WAFs alone may not be sufficient for preventing SQLi attacks, together with input sanitization, could drastically reduce the risk of your website being exploited.
A WAF that encounters a suspicious input, but is not malicious, may cross-check it with IP data before deciding whether to block the request or allow it. It only blocks the input if the IP itself has a bad reputational history.
-
Do not trust any input
You must treat all inputs, even from trusted sources, as potentially malicious inputs. Any input that can be mistaken for an SQL query should be handled with extreme caution.
-
Use whitelists instead of blacklists
Instead of blocking out notorious IPs and malicious users, only allow authorized users and sources to access the web server.
Whitelists will prevent all unauthorized personnel from accessing the SQL server and only allow those mentioned in the whitelist. Moreover, an experienced attacker can find methods to bypass the blacklist blockage, but whitelists are harder to circumvent.
-
Employ the latest protection technologies
Older web development technologies do not have built-in mechanisms for protecting against SQLi attacks. However, some of the newer technologies do. Therefore, it is advised that you choose the safest technologies available to you that have the latest definitions for security protection.
-
Restrict information in error messages
Most of the attackers rely on replies from the server when performing an SQL injection attack, which often includes error messages. If the error messages contain too much information, the attacker could exploit that to successfully manipulate the input and perform SQL queries. Therefore, as a developer, you ought to restrict the disclosed information in error messages to what is only necessary.
-
Use encryption
Encryption is the best method to protect sensitive information. Even if the data falls into the wrong hands, it is of no use to them without the appropriate decryption key. This is why, if you have sensitive information stored on the SQL server, it is advised that you use complex encryption standards to further protect your data from theft.
-
Perform regular updates
Like all software, the plugins and other components on websites also have regular updates released from the manufacturer. Be sure to install the updates regularly to ensure proper protection of the website, the SQL server, and all other assets.
The updates normally include security patches that fix any discovered vulnerabilities that could be explored by the attackers.
These are the methods for keeping your websites and SQL servers secure from SQL injection. As you may have already noticed, there is nothing you can do to prevent SQLi attackers directly. However, you can take precautionary steps and proactively block attackers from being able to exploit SQL vulnerabilities through these preventive mechanisms.
Ending words
SQL injection is considered one of the most dangerous attacks out there. This is probably because there is no defined damage an SQLi attack can do – it can be designed to perform any number of malicious activities, depending on the privilege level it achieves.
That said, there are several things you can do to reduce the risk of SQLi attacks on your website. However, the risk is never zero, and increasingly sophisticated attackers can come up with ways to bypass the most advanced security checks.