Infotech

All Types Of Cyber Attacks Explained
A cyber threat can go undetected if not careful. Here are all the types cyber attacks you should…

What Is Dirty Bit And How To Manage It in Windows
How can your computer know when a file or page has been modified by the system hardware, and…

What Are Windows Moment Updates And How Are They Different?
Confused about all the different Windows updates and what they mean? Here is what you need to know.

What Is Cryptojacking And How To Prevent It
Why let the attackers generate revenue off of your system’s resources? Here’s how to prevent it.

Difference Between Wi-Fi 7, Wi-Fi 6, And Wi-Fi 5
Learn what the fastest Wi-Fi standard has to offer and how it works before it is publicly made…

What Are Zero-Day Attacks And How To Prevent Them
Protect your devices from new and unknown threats using these methods, while the software manufacturer works on a…
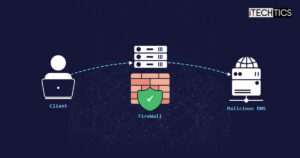
What Is DNS Tunneling And How To Prevent It
DNS data packets often go without being scrutinized, and could contain sensitive information if exploited. Here are the…

What Is SQL Injection And How To Prevent SQL Injection Attacks
Protect your websites and web applications from being exploited by SQL injection. proactively protect your assets by applying…

Types Of Password Attacks And Prevention Techniques
Stop your passwords from being cracked and deciphered with these password attacks. Implement the given best practices to…

What Are Drive-By Attacks And How to Prevent Them
Keep your websites and your systems secure from drive-by attacks with these prevention techniques.
