Network Security

All Types Of Cyber Attacks Explained
A cyber threat can go undetected if not careful. Here are all the types cyber attacks you should…

What Is Cryptojacking And How To Prevent It
Why let the attackers generate revenue off of your system’s resources? Here’s how to prevent it.

What Are Zero-Day Attacks And How To Prevent Them
Protect your devices from new and unknown threats using these methods, while the software manufacturer works on a…
What Is DNS Tunneling And How To Prevent It
DNS data packets often go without being scrutinized, and could contain sensitive information if exploited. Here are the…

What Is SQL Injection And How To Prevent SQL Injection Attacks
Protect your websites and web applications from being exploited by SQL injection. proactively protect your assets by applying…

Types Of Password Attacks And Prevention Techniques
Stop your passwords from being cracked and deciphered with these password attacks. Implement the given best practices to…

13 Types Of Malware And Prevention Techniques
Each type of malware behaves differently, and thus our devices need different protection checks and techniques. Here are…

How To Prevent All Kinds Of Malware Attacks
Protecting your devices from malware attacks is better than removing it after losing data, credibility, and financial losses.
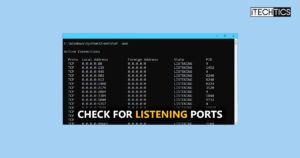
Check For Listening (Open) Ports With NetStat And PowerShell
Listening ports can be used by hackers to infiltrate your system without authorized access. When not in use,…
Search and Discover More
