Drive-by attacks, or “Drive-by download attacks,” are a type of cyberattack where malicious software is unknowingly installed and executed on your computer. This malware is normally transferred from a malicious website but can also be deployed using other means, like phishing emails.
It is known as a “Drive-by attack” because a user normally does not even need to interact with an infected website to catch the malware. All they must do is visit the malicious link and their devices are compromised. This makes a drive-by attack very sneaky, and therefore, very dangerous.
In this post we will learn everything there is to know about drive-by attacks, how they work, and more importantly, how you can protect your devices from them. This applies to both the website-web application owners as well as the end users.
This page covers
What is a Drive-by Download attack?
A drive-by attack is when you visit a malicious website and it automatically downloads and executes a malicious script of software onto your device. The malware could be intended for any number of purposes, such as damage your data, spy, encrypt the file, create a back door, etc.
This attack is often also known as a Drive-by Download attack. this is when the user needs to interact with the website and intentionally download something. Often, users download a legitimate software setup and accidentally download malware with it without knowing about it.
A website is normally injected with malware through exploiting vulnerabilities, like in a Cross-Site Scripting attack. Normally, the owner of the website is unaware of exploitation and the end users that visit the infected website end up being the real victims.
Types of Drive-by attacks
The drive-by download attacks are of two types. These types are defined by how the malicious content makes its way onto the end-user devices. The major two types of drive-by attacks are:
- Attack without authorization
- Attack with authorization under false pretenses
The former, “attack without authorization,” is when the malware is deployed without the user knowing about it. This is usually in the case of drive-by attacks, where the user isn’t required to interact with a website for the malware to execute. Therefore, without the end-user authorizing the download, the malware still finds its way onto the device.
The latter, which is “Attack with authorization under false pretenses,” is when the end-user intentionally downloads something that seems legitimate, but in reality, isn’t. In such a case, malware could be disguised as legitimate software, or the attacker could have planted malicious code inside valid software, or attached it to it. The user then downloads and executes the malware, without knowing what they have agreed to.
This kind of attack is usually delivered through adverts, malware disguised as a legitimate link, or a phishing email containing a malicious link.
How Drive-by attacks work
Drive-by attacks normally start from a website. However, if it is a drive-by download attack, then other delivery methods can also be adapted, such as ads, malicious download buttons, etc. Here is a complete step-by-step of how drive-by attacks work:
-
Compromising a website
The first phase usually involves compromising a website. Attackers search websites for any existing vulnerabilities that could be exploited. These are usually found on websites that have not been maintained for a while, and the latest patches have not been installed. When a vulnerability is found, the attackers compile a code to exploit it and plant their own malicious code.
-
User visits the malicious page
The next phase initiates when an end-user visits the web page. The malware is downloaded automatically (in the case of a non-download drive-by attack) and executed, compromising the device.
-
Malware is executed
Once the malware is executed, it does its job. The malware could be coded to perform any number of malicious activities, ranging from simply spying on your activity to spreading throughout the network like a worm.
How to prevent Drive-by attacks
Preventing a cyberattack from occurring is always better than having to clean up and recover after it has already happened. Therefore, it is in your best interest to protect your assets, including data, and prevent Drive-by attacks from happening in the first place.
As mentioned earlier, the prevention methods need to be implemented on both the website end, so that they are not compromised, as well as the user’s end.
How to prevent Drive-by attacks on websites
If you are a website owner, then you can adopt the following recommendations to keep your website safe to prevent attackers from exploiting it:
-
Take all XSS-attack precautions
In an XSS attack, the attackers target a vulnerable website and inject their malware, which in turn affects the users that visit it. An XSS attack can be used to plant malware into a website and deliver it to the end users. You can take the following precautionary measures to make sure that your website is safe from XSS attacks:
-
Keep website components updated
Updates usually include security patches, which patch up known and unknown (zero-day) vulnerabilities. Therefore, it is always recommended to install updates as soon as they are available. However, we do advise that you go through the release notes for the update to look out for any potential additional threats or loopholes in its security.
-
Use security software
Websites use plugins for additional features, support, as well as security. We advise website owners to use reliable and reputed security plugins to make sure that their website is impenetrable.
-
Monitor your adverts
Many websites use adverts to generate revenue. Keep a lookout for what kind of adverts the end users visiting your website are seeing, and keep a lookout for any malicious ads that may include redirections to malicious websites or inappropriate content.
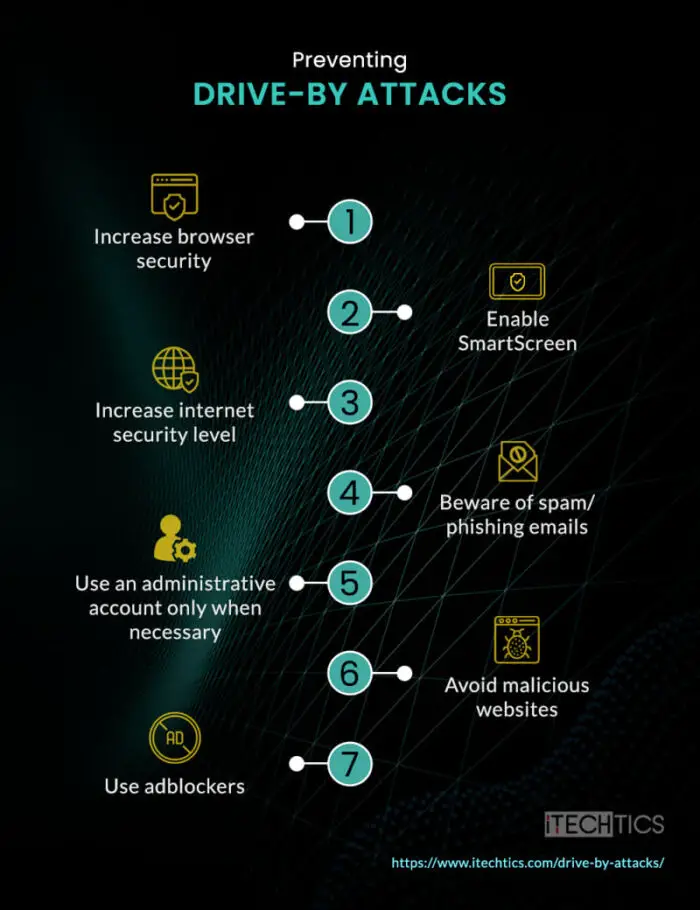
How to prevent Drive-by attacks for end devices
For end devices, here are the prevention techniques you can adopt:
-
Take all XSS-attack precautions
Similar to website owners, end-users must also take the necessary precautions that prevent XSS attacks. here are the things you should do:
-
Use an administrative account when necessary
Administrative accounts have the privilege to change system settings, including critical security options. If malware is executed through an administrative account, it is likely that it will also have the same level of privileges. Therefore, it is advised that you use standard accounts at all times unless administrative rights are absolutely needed.
-
Avoid malicious websites
Visiting or downloading from unknown websites, especially those that contain questionable content, should be avoided at all costs. You never know what action will cause your device to be compromised.
-
Use adblockers
Most of the time, ads are usually a method of delivering and planting malware. Intentional or unintentional clicks on ads can often reroute you to malicious websites, and your device is infected even before you can react. Therefore, it is advised that you use adblockers to eliminate the ads.
Final verdict
Drive-by attacks can be of any sort and any severity, which makes them even more dangerous. You may never know what type of malware it carries and what impact it can have. Therefore, be wary of obscure websites that are not publically known.
That said, even if you implement all of the prevention techniques given in this post, there is no guarantee that your device will be protected when it does face a drive-by attack, which is why we recommend that both the website owner and the end users do their part in making sure that their assets are well-protected.