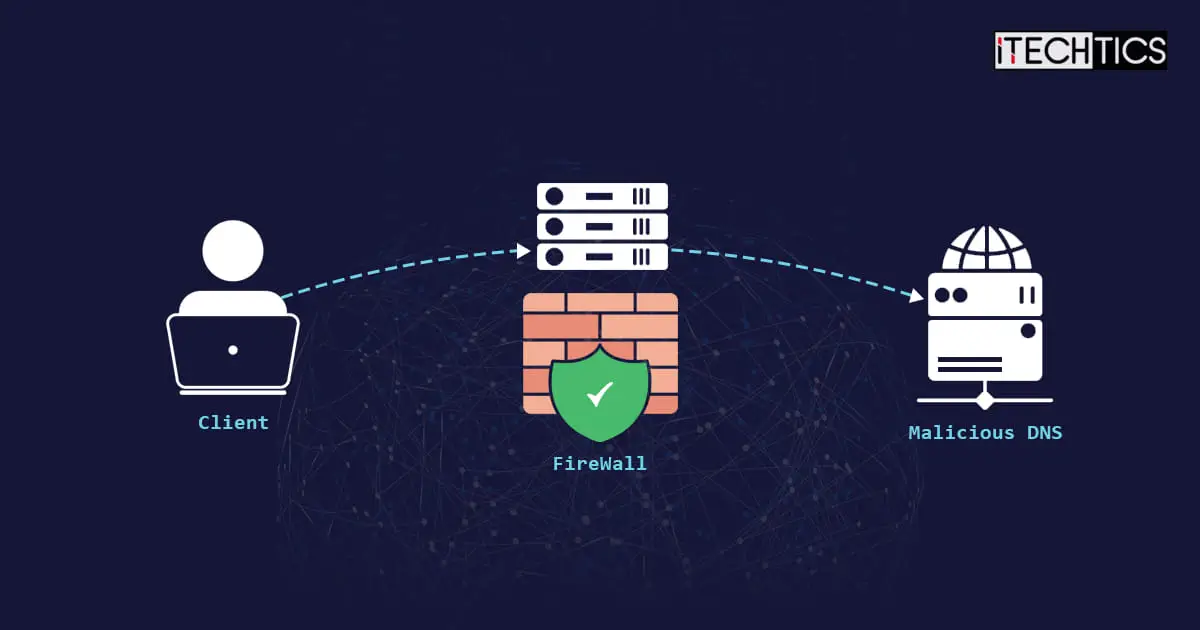
A Domain Name Server (DNS), is a server that resolves the IP addresses against a domain name. Since it is impossible for everyone to remember the long IP address for each domain, like www.itechtics.com, a DNS automatically provides the corresponding IP for a domain name by performing a lookup.
DNS tunneling is a type of cyberattack where the attacker takes advantage of the fact that most DNS traffic is unsupervised and can easily go past even the most complex firewalls. In such an attack, the stolen information is encapsulated in the DNS queries and responses, and thus, allowed by firewalls to pass through, undetected.
Whether you are a home user or an employee of an organization, you can fall victim to DNS tunneling. Since it is a hard-to-detect cyberattack, it is in your best interest to know what it is, how it works, how to detect a DNS tunneling attack, and how to prevent it from happening.
This page covers
What is DNS tunneling?
DNS tunneling is a form of cyberattack where sensitive information is stolen. Normally, this information is behind secure firewalls and cannot be accessed using conventional unauthorized methods. Thus, the attackers need to take a more desperate approach and steal that information with DNS tunneling.
In DNS tunneling, an attacker infects a target computer with malware which then makes a connection to the attacker’s DNS server, from where they control the traffic. Thus, DNS data packets, that go unmonitored and undetected behind firewalls, contain sensitive information that is being smuggled to the attacker.
The incoming DNS packets contain commands, and the outgoing DNS packets contain the sensitive information that the attacker wants. The attacker might also acquire a domain, whose domain server is used to redirect the traffic to the attacker’s DNS server.
Since the regular DNS traffic uses port number 53, any data encapsulated with the same data will automatically use the same port as well.
How DNS tunneling works
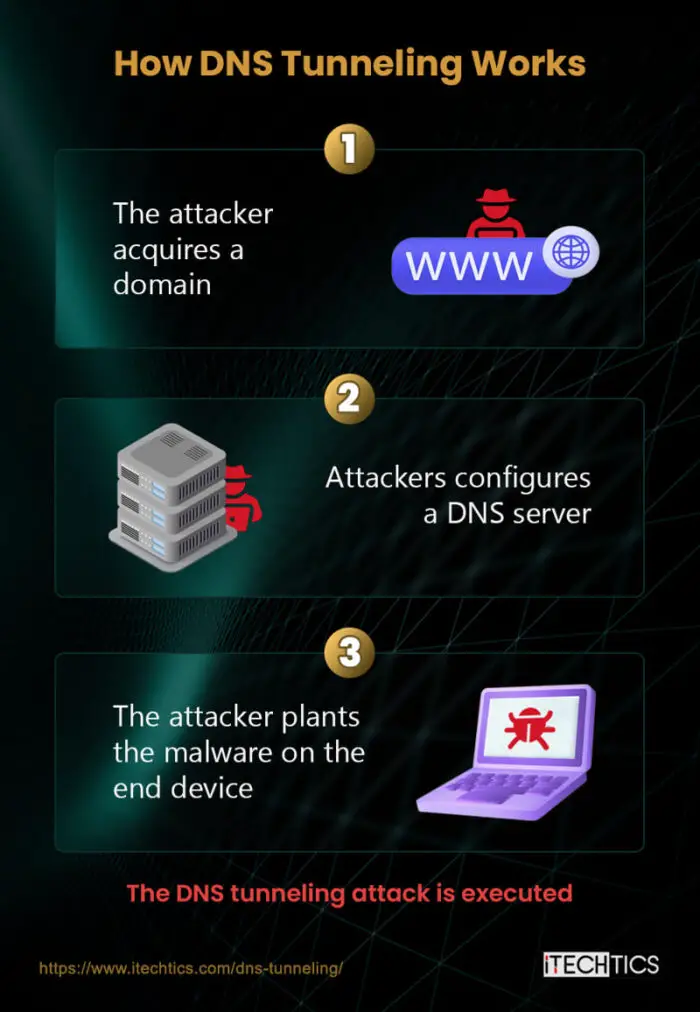
A DNS tunneling works with a client-server model. The attacker needs a DNS server that is under their control, and a client machine that they can exploit. There are several steps involved while performing a DNS tunneling attack.
-
The attacker obtains a domain
The first step of the process is obtaining a domain for malicious purposes. An attacker purchases a domain, whose name server is then used to redirect the traffic onto the attacker-controlled DNS server.
-
Set up a DNS server
The next phase of the process is setting up a DNS which is under the attacker’s control. Using this DNS, the attacker communicates with the client device which has been compromised.
-
The attacker plants the malware
Another major step in the attack is executing malware in the client device. Normally, this device is behind an organization’s firewall, and thus, other techniques need to be adopted to plant the malware, like phishing.
The client PC sends a request to the DNS resolver, and since there are no restrictions on DNS traffic, the data packets are forwarded to the malicious DNS server, instead of a legitimate one.
-
The DNS tunneling attack is carried out
Once a connection has been established with the attacker’s DNS controller, they continue to send data packets back and forth, sending commands and obtaining sensitive data.
This is how a DNS tunneling attack is carried out. Now, if the security professionals at the organization have a keen eye, they could figure out that an attack is being executed. However, if they lack the basic training and have no proper security checks in place, then the attacker could continue to send DNS packets back and forth without being detected.
How to detect and prevent DNS tunneling
As mentioned earlier, DNS tunneling is a hard-to-detect attack, since all of the processes are occurring in the background. The DNS packets are tiny, and thus, the client device gives no significant indication of whether the resources or the bandwidth are being significantly used.
On top of that, most firewalls are allowed to let through almost all DNS requests, since a user could potentially look up any domain name. Therefore, without proper monitoring, even the firewalls allow the malicious DNS traffic to pass through.
Hence, the only way to monitor DNS tunneling is by continuously observing the DNS traffic. There are DNS monitoring and payload analysis tools that will split open the data packets to see what’s inside. Here are a few known DNS monitoring tools:
- SolarWinds Server and Application Monitor
- ManageEngine Applications Manager
- Paesler PRTG Network Monitor
- DNS Check
Using these tools, you can keep a constant eye on your DNS traffic and set alerts for any irregular activities. Note that some of these deep packet inspection tools can cause delays, resulting in slower internet speeds, since the tools need to split open the packets and inspect them for malicious content.
With these tools, you can keep a lookout for the following characteristics of DNS packets:
- Unusual domain requests: The data is encoded within a requested domain name which may seem unusual, like “Data_Content.maliciousdomain.com”, and such traffic can help you differentiate between legitimate and malicious DNS traffic.
- Uncommon domain names: DNS tunneling only works when the attacker has their own DNS. If you see unusual domain names within the DNS packets, it could potentially indicate a DNS tunneling attack.
- Unusually high DNS traffic: Sudden spikes in DNS traffic could mean a potential DNS tunneling attack, as the attacker is communicating with the compromised client via DNS data packets.
These are the things you must keep an eye out for in case of a DNS tunneling attack. To proactively prevent an attack, these are the best practices:
-
Block notorious domains and IPs
You can use blacklists to block access to malicious domains and IP addresses that you are already aware of. There is plenty of information on the internet about known attacks, and the domains/IPs used during those attacks. This way, you can proactively block possible DNS tunneling attacks.
-
Set firewall rules to block certain DNS queries
You can configure rules in the firewall to automatically block DNS traffic if certain data strings are found inside any packets. Similarly, you can also block traffic based on the length, type, and size of the inbound or outbound DNS queries.
-
Provide phishing training
Since one of the steps of a successful DNS tunneling attack includes planting malware on a client device, you must ensure that all the organization’s employees have sufficient training to protect their assets and data against phishing and spear phishing techniques.
-
Use advanced network monitoring tools
Constant network monitoring is a critical component for both detecting and preventing DNS tunneling attacks, otherwise, they could go undetected. Therefore, it is advised that you use a sophisticated networking monitoring tool that alerts the security professionals when an anomaly is detected.
Conclusion
DNS tunneling is perhaps the simplest form of cyberattack. However, it is still one of the healthiest ones out there. This article tells you everything there is to know about DNS tunneling attacks, including how it works and the steps involved. It also informs you of ways to prevent DNS tunneling attacks so that you do not fall victim to them.
For both the detection and prevention of DNS tunneling attacks, it is advised that you use professional-grade network monitoring and payload analysis tools to monitor the DNS traffic. These tools are normally paid, and thus, only large-scale organizations use them.
Regardless, if you have fallen victim to such an attack, it is advised that you take the required preventive measures, protect your assets even behind the firewall, and use such sophisticated tools.