Windows Security, formerly known as Windows Defender, is Windows-native antivirus software that keeps your system protected all around. It has been considered a reasonable protection software sufficient to protect a PC, thus not requiring additional software to add another layer of security.
Now, Microsoft has added another feature to Windows Security: a driver block list named “Microsoft Vulnerable Driver Blocklist“
With this feature, Windows can now block drivers from running on your PC, which can be a potential threat to it. Since Microsoft has a zero-tolerance policy for malicious code execution in the kernel of the operating system, with the driver block list activated, it automatically prevents drivers and other pieces of code from running on it.
Let us dig a bit deeper into the details of this new Windows Security feature.
Windows Security Vulnerable Driver Blocklist
Microsoft works closely with Independent Hardware Vendors (IHVs) who need to get their drivers approved before they can be sent to the public through Windows Update. Therefore, those drivers are pre-verified and completely safe to run on your PC.
However, malicious drivers can be blocked through the new Windows Security driver block list. This is a list compiled by Microsoft itself that blocks such drivers from running on your computer. Drivers are considered malicious if they have any of the following attributes:
- Known security vulnerabilities that can be exploited by attackers to elevate privileges in the Windows kernel
- Malicious behavior (malware) or certificates used to sign malware
- Behaviors that are not malicious but circumvent the Windows Security Model and can be exploited by attackers to elevate privileges in the Windows kernel
If a driver has any or all of these attributes, it will be added to the blocklist by Microsoft and released into the Windows ecosystem. Microsoft does not allow you to block drivers manually, since blocking critical system drivers can cause devices or software malfunction, or even cause a Blue Screen of Death (BSoD).
That said, the Windows Security driver blocklist has some requirements that need to be satisfied for it to work, which is why it can only be allied to the following operating systems:
- Windows 11
- Windows 10
- Windows Server 2016 and later
Microsoft Vulnerable Driver Blocklist is dependent upon the Core Isolation feature of Windows Security known as Memory Integrity, which in turn relies on Microsoft Hyper-V and is used to protect critical Windows kernel-mode processes. This does not mean that you need to enable Hyper-V through Windows optional features.
Let us now show you how to enable this feature on a Windows machine.
How to Enable Microsoft Vulnerable Driver Blocklist
When the feature was first shipped, it was disabled by default. However, Microsoft then enabled it on the following devices by default:
- Windows 10 S-Mode
- Devices with Hypervisor-Protected Code Integrity (HVCI), also known as Memory Integrity, enabled.
It can be argued that the feature is best suited for organizations and companies who want to keep their environments safe. However, it is highly unlikely that they will be running Windows 10 in S-mode. Hence, you must enable Memory Integrity on your Windows 11/10 PC using the following steps:
-
Navigate to the following:
In Windows 11:
Settings app >> Privacy & security >> Windows Security >> Device Security
In Windows 10:
Settings app >> Update & security >> Windows Security >> Device Security
-
Here, click on Core isolation details under “Core isolation.”
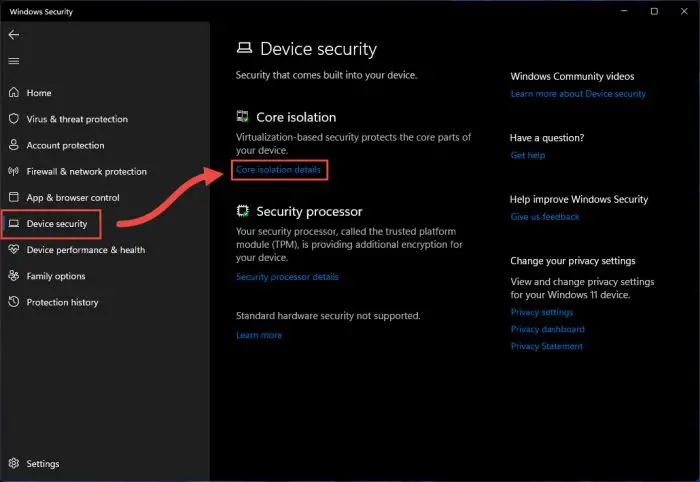
Core isolation details -
Here, toggle the switch into the On position beneath Memory Integrity.
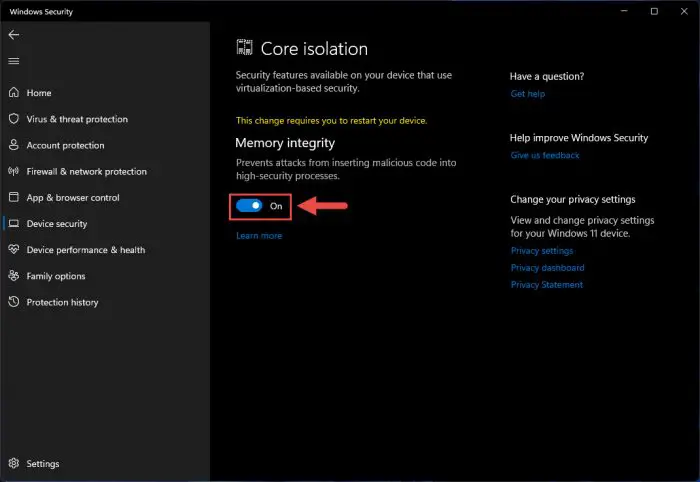
Toggle on memory integrity -
Now restart your computer for the changes to take effect.
Once the computer reboots, Memory Integrity will be enabled, and drivers predefined by Microsoft will be blocked. You can now activate or deactivate this feature as you please. However, it is recommended that you keep it enabled.
That said, there may be instances where you are unable to enable Memory Integrity due to an incompatible driver installed on your system. If so, the section below discusses how to resolve the problem.
How to Enable Core Isolation Memory Integrity in case of Incompatible Driver
Experiencing problems while trying to enable Memory Integrity may look something like this:
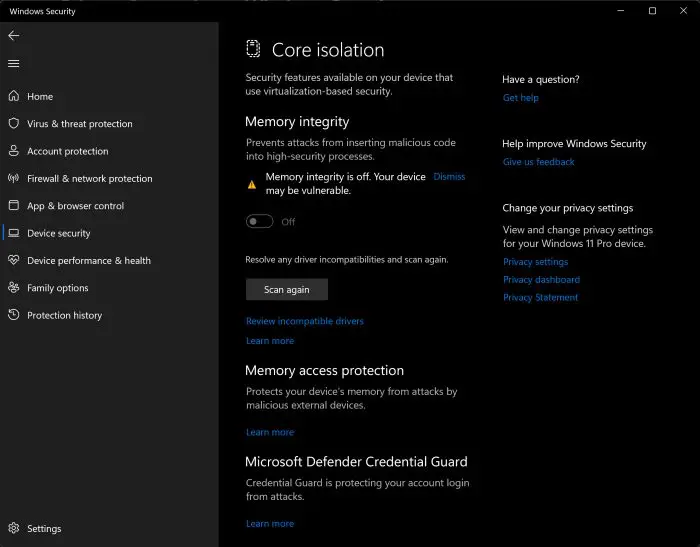
This means that one or more drivers installed on your computer are rendering the feature incapable of protecting your PC. In that case, the driver(s) needs to be uninstalled. To begin, you must first identify the problematic driver.
Follow these steps to fix the Core isolation issue and enable Memory Integrity:
-
From the Core Isolation page, click Review incompatible drivers.
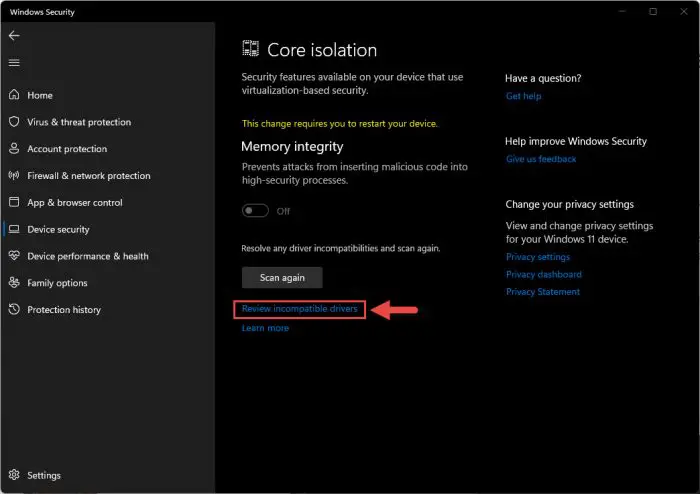
Review faulty drivers -
Now click on the listed driver and then note down its “Published name.” This will be required further down the process of removing this driver.
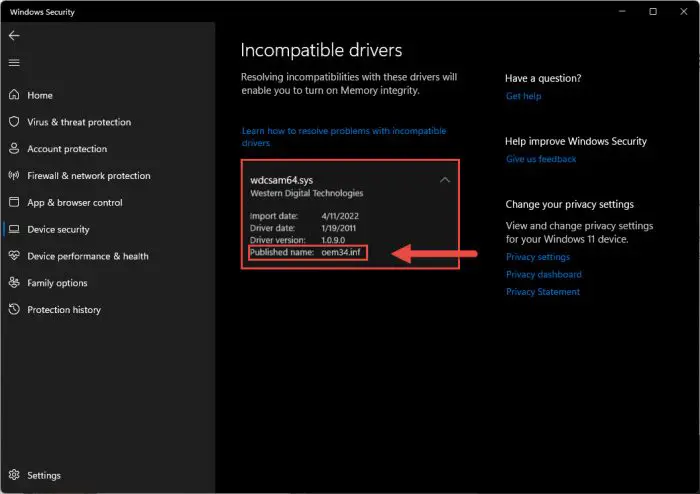
Note down name -
Now open up the Device Manager by typing in devmgmt.msc in the Run Command box.
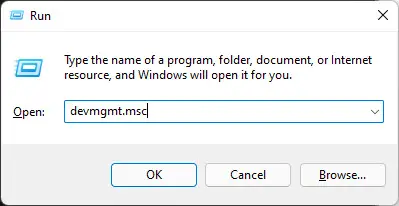
Open Device Manager -
Click View from the top menu, then select Devices by driver from the list.
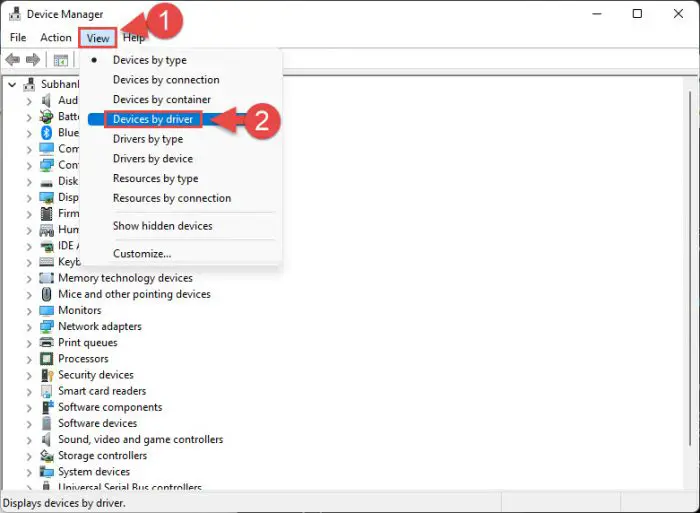
Change view type -
Now look for the noted driver from step 2 above in the alphabetically-sorted list below. When found, right-click it and then click Remove driver from the context menu.
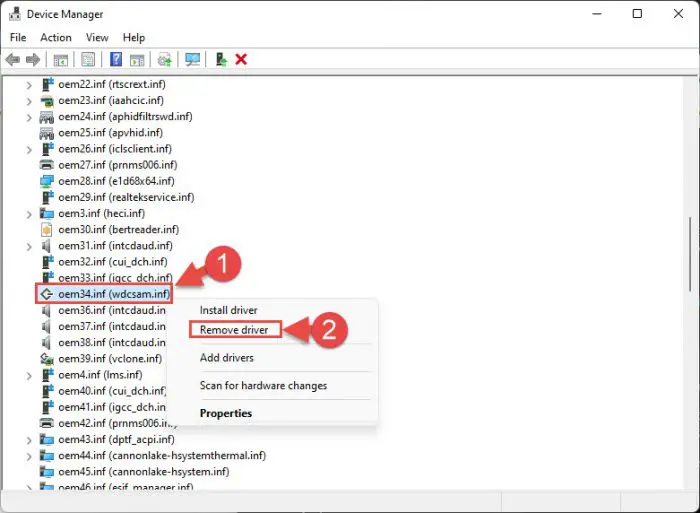
Uninstall driver -
From the popup window, make sure that both boxes are checked. Then click Remove.
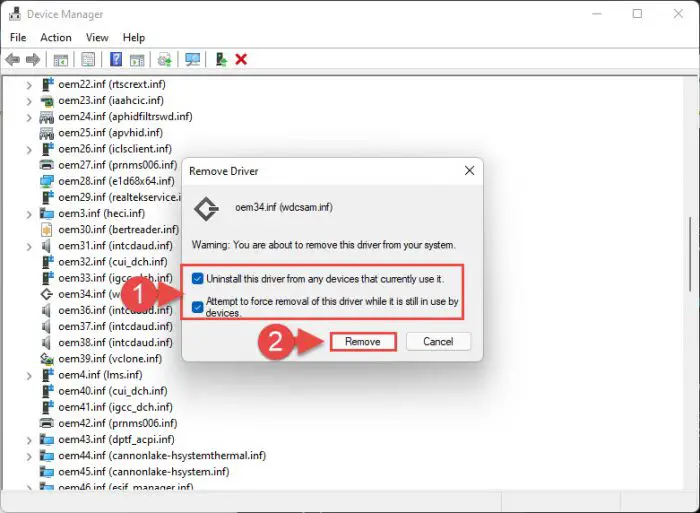
Confirm removal The driver will now be uninstalled successfully.
-
Now return to the Core Isolation page and click Scan again.
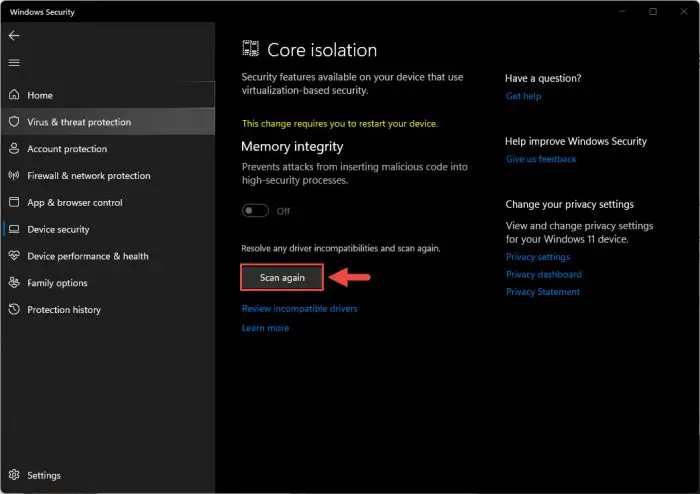
Perform scan again
That’s it! The system will perform a quick scan, and as soon as it detects that the incompatible driver has been taken care of, it will enable Memory Integrity automatically.
Final Thoughts
Driver updates received through Windows Update are signed by a trusted party or by Microsoft itself. Therefore, they are considered free from any virus and threats. However, attackers often target unsigned drivers and penetrate your network through them, which is why Microsoft takes such threats seriously.
You can find the XML file here which contains the list of blocked drivers ready for use, and also which Microsoft uses through Memory Integrity.