Cybersecurity was relevant today, has been relevant for decades, and will be increasingly important in the future as well. If you use a computer or smartphone, whether or not it is connected to the internet, cybersecurity should be one of your main concerns.
Nowadays, phones have locks (biometric, PIN, pattern, etc.), computers have encryptions and passwords and are usually placed at a safe location. For example, a computer may be locked away in your office, and a phone may be on-person. These are all methods to keep increasing the physical aspect of the device’s cybersecurity.
Mind you, no one has forced you to implement these security checks – these are just the general rules and best practices to keep your devices secure. Similarly, there are documented guides and best practices put together by leading IT specialist bodies to enhance your cybersecurity, which are known as “cybersecurity frameworks.”
In this post, we discuss what cybersecurity frameworks are, their types, why they are important, and who can benefit from them. By the end of this post, you will have learned about the major cybersecurity frameworks and what each of them holds.
This page covers
What is a cybersecurity framework?
When you talk about a framework, non-technical users may think of it as something physical and tangible. For instance, the framework for a building would be the thick metal or concrete structure around which the building is constructed. However, that is not the case when referring to cybersecurity frameworks.
A cybersecurity framework is a set/combination of guidelines, best practices, and the do’s and don’ts for cybersecurity threat prevention and management. These rules and policies are used to guide organizations, as well as individuals to perform risk assessment, reduce the threat impact, and such.
A cybersecurity framework is constructed after thorough discussions, feedback, and real-world scenarios and then branded a “framework.” Different types of cybersecurity frameworks exist, and each type can have multiple frameworks.
While some cybersecurity frameworks can be applied to any size of organization, other frameworks are put together for specific countries. For instance, the UK can have its own standards of cybersecurity protection and policies, and thus, has its specific framework to which all IT companies must adhere under the laws of the UK.
Why are cybersecurity frameworks used?
As implied above, a cybersecurity framework is a predefined guideline on what rules and policies to implement to make your networks and systems secure. Rather than starting from scratch, with frameworks, you already know how to make your system as secure as possible, what practices to implement, what training to give (or learn), etc.
A cybersecurity framework also sets the standards for individuals and organizations by creating a culture of security and minimizing risk factors. This, in turn, not only help keep the organization in check by the governing bodies but also keeps the companies and their client’s data secure.
A framework defines how to approach the subject and implement the best practices to protect the system and its assets from potential cyber threats. They help cybersecurity professionals with the techniques, methods, and policies to implement so that they can reduce the attack surface and manage the threats promptly while reducing the impact to a minimum.
Types of cybersecurity frameworks
We mentioned earlier that there are different types of cybersecurity frameworks. These are categorized by what a framework does. Does it protect assets, or does it make the network secure and invulnerable to outside threats?
There are 3 main types of cybersecurity frameworks:
- Control frameworks:
- Control frameworks are used to define the basic set of rules and policies for the security team. These include checklists, procedures, maintenance details, etc. It includes the basic strategy to adapt. Additionally, a control framework also assesses the current state of the system infrastructure for risk management.
- Program frameworks:
- A program framework is that which consists of a program that improves the overall security of the system. This typically starts with the assessment of the existing cybersecurity infrastructure, after which a plan is devised. The program can include simplifying communication between security professionals and upper management, providing training to employees from becoming a victim of phishing scams, etc.
- Risk frameworks:
- All frameworks that assess, quantify, reduce, and manage risks are risk frameworks. These include governance, risk management, and compliance, which essentially translates to assessing, managing, and then implementing risk-reduction policies. Frameworks that are used to identify, measure, and quantify fall into the risk framework category, and may also include the processes for risk assessment and management.
A framework doesn’t need to satisfy all of the above-mentioned conditions to fit within a category. However, unless customized, it is very unlikely that a known cybersecurity framework will fit more than one category.
That said, below we have shared the details of some of the popular, known, and well-adapted cybersecurity frameworks.
Crucial cybersecurity frameworks
Below you’ll find some of the popular and renowned cybersecurity frameworks currently implemented today around the world. These include all 3 types of frameworks discussed above. However, each one of these is designed to protect different components within the system.
For example, while one framework is designed to secure the complete intranet, another may be focused on protecting the assets within the network.
NIST Cybersecurity Framework (CSF)
NIST stands for “National Institute of Standards and Technology.” This is America’s governing body that standardizes rules, policies, and regulations nationally. The official, public release of this NIST Cybersecurity Framework (CSF) came in 2018 after the Obama administration ordered to protect all of America’s critical infrastructure from cyberattacks, such as dams, power plants, etc.
The NIST CSF is designed for both new organizations and existing enterprises so they can secure their intellectual and physical assets from cyberattacks. This framework consists of a plethora of rules, policies, and best practices that help better the cybersecurity infrastructure of a system.
CSF is considered one of the most popular and crucial frameworks as it sets the tone for the company’s security by assessing and managing its core security infrastructure. Although it was designed for America’s national assets, it is widely adopted across borders.
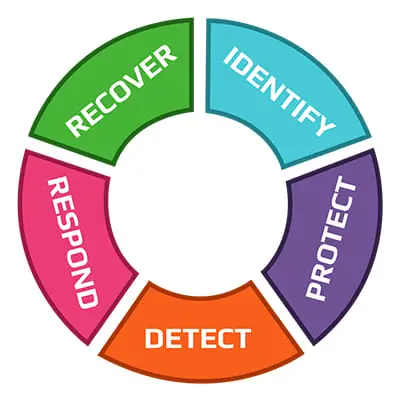
The NIST CSF is based on the following 5 principles:
- Identify
- Protect
- Detect
- Respond
- Recover
As per the framework, these are to be implemented and adhered to in the same order. You will understand why it is important to observe this order once we explain the principles in detail.
NIST CSF: Identify
Identification is the first portion of the NIST Cybersecurity Framework. It means that you need to start with identifying the assets (physical and software), as well as the processes that you must absolutely protect.
The identification process is the core of the framework. Therefore, it needs to be performed with total focus. Once you identify the objects, only then will you be able to protect them, detect any threats, respond to the threats, and perform a full recovery.
Note that the identification must not be limited to the tangible objects only – but also the core ideologies. For example, you must also identify the crux of the business so it can be protected, and a business continuity plan could be carried out.
The following activities need to be carried out during the “identify” phase:
- Identifying physical and virtual assets. This is needed to establish the basis of an asset management program.
- Identifying the organization’s business ideology.
- Identifying already-established cybersecurity policies to help fabricate the governance program as well as identifying legal and regulatory requirements regarding cybersecurity capabilities.
- Identifying asset vulnerabilities, threats to resources, and risk response activities.
- Identifying risk tolerance thresholds.
- Identifying a supply chain risk management strategy including priorities, constraints, and risk tolerances.
NIST CSF: Protect
Once the assets and the resources have been identified, you must now protect them, from all sorts of threats. These can be physical as well as cyber threats.
The “Protect” portion of the framework discusses how to ensure the safeguarding of the identified assets. These practices will help keep the assets secure in the event of an unauthorized breach, natural disaster, or any other unforeseen threat.
This part of the framework includes the following activities:
- Install protection for Access Control and Identity Management within the organization including physical and remote access.
- Provide competent training to staff and employees for data protection, phishing scams, and other practices to protect assets.
- Establish data protection policies that are consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information.
- Implement procedures to manage and maintain the protection of information systems and assets.
- Perform routine maintenance to protect organizational resources, including remote maintenance activities.
- Implement technological policies to ensure the security and resilience of systems, consistent with organizational policies and procedures.
NIST CSF: Detect
In the real world, where proper frameworks are not implemented, cyberattacks are gone undetected. Only after some while, when critical user data is being auctioned on the dark web, does the organization realize that their data has been hacked.
Therefore, the NIST CSF includes a “detection” guideline that ensures that the proper checks and balances are in place that immediately inform the security teams of irregular activity.
This portion of the framework includes activities like continuous monitoring of the network traffic and assets, in-place alerts of irregular uploads or downloads, alerts and notifications of unauthorized access requests, etc.
Of course, once an incident is detected, only then can you respond to it.
NIST CSF: Respond
The “response” function of the framework provides guidelines on taking the appropriate action to minimize the impact of a threat if it occurs. This portion of the plan is usually implemented during and after a cybersecurity incident has occurred. This portion consists of activities such as:
- Reducing the attack surface and preventing the incident from spreading across more resources.
- Analyze the threat and immediately respond with appropriate actions.
- Perform mitigation activities to prevent the expansion of an event and to resolve the incident.
- Constant communication with stakeholders to get ahold of the situation promptly.
- Improving the system protection after learning from prior mistakes.
NIST CSF: Recover
The “recovery” portion of the framework comes after there has been a cyber incident. This section does not necessarily mean data recovery, but also recovering from any downtime of the assets on the network.
The NIST CSF highlights the best practices and norms to adhere to in case of a cyber attack, and how you can overcome it, and learn from it to prevent future attacks. this portion usually includes the following activities:
- Restoring all network connections and assets to normal functionality.
- Improve existing infrastructure and framework policies after learning from previous breaches.
- Perform forensics to analyze the attack so the incident is not repeated.
These are the 5 pillars of the NISTT CSF that can help you improve your existing network’s security or can be used to build up your security infrastructure from scratch.
ISO/IEC 27001 and 27002
The International Organization of Standardization (ISO) has created two cybersecurity frameworks: ISO/IEC 27001 and ISO/IEC 27002. Together, these two standards hold great significance in ensuring a company’s ability to protect data. These are also one of the most commonly-adopted frameworks by the companies that handle user data.
The ISO 27000 series frameworks are for companies that use Information Security Management Systems (ISMS). An ISMS is a set of rules and policies that ensures that sensitive data is protected by international standards. On top of this, the ISO 27001 and 27002 frameworks signify that the data holds its integrity and is handled by a well-protected and risk-assessed system.
That said, unlike NIST CSF, you cannot simply claim to adopt the ISO 27001 and 27002 standards. Instead, you need to follow the defined practices and procedures, after which you must request an audit from one of the assigned auditors in your area. Once you have passed the audit, only then can you achieve the status of ISO/IEC 27001 and 27002 certification.
If you are wondering why there are two separate standards by ISO for the same thing, your concern would be valid. ISO 27001 is a standard that guides how to approach risk assessment, control selection, and policy/rule implementation. It tells the requirements for establishing an ISMS.
On the other hand, ISO 27002 is not a standard, but a code of practice that highlights the details of security control practices.
When an organization has both these certifications, it can be assumed that any data which the organization holds or handles is in safe hands.
CIS Control Framework
Published in the late 2000s, the Center for Internet Security (CIS) Control framework is still valid through regular updates. The CIS framework is used to protect a network from cyberattacks and covers areas like access control and management, asset management, incident reports and responses, etc. It is a set of 20 controls that include the following:
- Data protection and integrity
- Audit log management
- control of inventory and assets
- Defenses against malware
- Penetration testing
Unlike the NIST CSF, the CIS Control framework focuses solely on reducing cyber risks and increasing resilience, instead of performing a risk analysis. These controls are divided into three main categories as follows:
- Basic controls: These are the fundamental cybersecurity precautions that any organization has to take, such as regular patch updates, antivirus security, etc.
- Foundational controls: These more sophisticated safeguards which include two-factor authentication and routine checking of generated logs for suspicious behavior. These controls are to be implemented in addition to the basic controls.
- Organizational controls: These are the controls that are created to offer extra security measures tailored for the individual organization, such as user education and awareness, protocols to follow, etc.
The framework’s guide does not end here. It then goes further into defining three different implementation groups targeted at different-sized organizations.
Organizations with minimal resources and cybersecurity experience should use “Implementation Group 1”. Organizations with a reasonable amount of resources and cybersecurity knowledge should adopt “Implementation Group 2”. “Implementation Group 3” is for established businesses with ample resources and cybersecurity know-how.
Service Organization Control (SOC) Type 2
Service Organization Control (SOC) Type 2, also known as “SOC2,” is a comprehensive security framework centered around auditing controls and policies for organizations that handle client data. This is especially implemented for companies dealing with online transactions and sensitive financial information, and performed by licensed third-party auditing firms.
This framework was created by the American Institute of Certified Public Accountants (AICPA) and consists of 60 compliance requirements. At times, a detailed audit can take up to a year, after which the company is awarded a certification of framework adaptation.
The SOC2 framework assesses the confidentiality, security, availability, processing integrity, and privacy of the organization’s systems and services. This is what each of these trust services of the SOC2 framework includes:
- Security: Network and assets are protected against unauthorized access and infiltration, or any sort of data leakage.
- Availability: Data and information are available with minimal downtime.
- Processing integrity: Ensuring that the data processing is end-to-end safe, accurate, valid, timely, and meets the standards.
- Confidentiality: The client data is protected during all stages and is kept confidential, internally and externally.
- Privacy: Personal data is protected and kept confidential, used where required to meet the objective, and then disposed of properly without loss of integrity.
Additionally, SOC2 gives a comprehensive outcome of the framework implementation, as it describes how an organization’s system function over a period of time, instead of at any single point in time.
HITRUST Common Security Framework (CSF)
HITRUST stands for “Health Information Trust Alliance” – a collaborative organization governed by leading healthcare representatives. The HITRUST Common Security Framework, often referred to as the Cybersecurity Framework, is a set of best practices that create a standard for protecting the security of patient information and data.
The control policies of the HITRUST CSF are spread across 14 different categories and have a total of 156 control specifications. Since it is an elaborative certification to obtain, many healthcare organizations only attempt to obtain certifications in the smaller areas of the framework.
The table below highlights the division of control requirements, control objectives, and control categories within the HITRUST CSF:
| Category No. | Control Category | Control Objective | Control Specification |
| 1 | Information Security Management Program | 1 | 1 |
| 2 | Access Control | 7 | 25 |
| 3 | Human Resources Security | 4 | 9 |
| 4 | Risk Management | 1 | 4 |
| 5 | Security Policy | 1 | 2 |
| 6 | Organization of Information Security | 2 | 11 |
| 7 | Compliance | 3 | 10 |
| 8 | Asset Management | 2 | 5 |
| 9 | Physical and Environmental Security | 2 | 13 |
| 10 | Communications and Operations Management | 10 | 32 |
| 11 | Information Systems Acquisition, Development, and Maintenance | 6 | 13 |
| 12 | Information Security Incident Management | 2 | 5 |
| 13 | Business Continuity Management | 1 | 5 |
| 14 | Privacy Practices | 7 | 21 |
As you can derive from the table, the largest control scopes belong to the communications category. Therefore, it is safe to assume that most threats are present when patient data is being transferred between people through different mediums.
Since the Common Security Framework is a certification, it is granted by authorized third-party vendors who audit your organization before providing the certification.
Additionally, there are many other guidelines available within the HITRUST CSF, such as the categorization and determination of risk factors, defined architecture of the control categories, and much more. To learn more in-depth, download the HITRUST CSF documentation from the Quick Links above.
Quick Links
The COBIT framework was created by Information Systems Audit and Control Association (ISACA), and the latest framework update came with COBIT 5 2019 (since it was released in 2019).
COBIT framework provides elaborative, end-to-end guidelines designed to help organizations manage their IT resources more efficiently and effectively. This framework offers best practices for governance, risk management, and security. This framework functions on the following 6 governing principles:
- Meet stakeholder needs: The governing systems should be tailored to incorporate the stakeholder’s needs, which in turn will generate value. Value creation is possible by balancing resources, benefits, risks, governance systems, and actionable strategies.
- Have a holistic approach: The overall system should be interoperable, working in tandem, and have different parts.
- Dynamic governance system: Not all scenarios fit the same conditions. All governing policies must be tailored according to the current conditions and circumstances, and not be fixed.
- Distinct governance from management: There should be no overlap between IT management and governance. They both should be different and well separated from each other.
- Tailored to the organization’s needs: The overall system should be designed while keeping the organization’s interests at heart. This goal is achievable by pre-defining the customization and prioritizing the components used within the system.
- End-to-end governance system: The system has to be extensive enough to feature all the IT functions, data, technology, and assets that an enterprise has to use to attain the desired goals.
Other than the basic pillars of the COBIT framework, there are also five major categories through which the control system is divided, which are as followings:
- Evaluate, Direct, and Monitor
- Align, Plan, and Organization
- Build, Acquire, and Implement
- Deliver, Service, and Support
- Monitor, Evaluate, and Assess
For IT administrators, COBIT is more than just a list of technical requirements. This framework supports the requirements of businesses via combined IT applications, related processes, and sources. The parameters it provides can be divided into two main categories:
- Control: This includes the IT management policies, practices, procedures, and structures. These ensure that the business goals will be achieved.
- IT control objective: This states the acceptable results level that must be attained when implementing control procedures for a particular IT operation.
The COBIT guidelines do not end here. It also includes crucial components that set the bar for designing the actual framework. It discusses what considerations to keep in mind whilst implementing the governance system.
Cyber Essentials (UK)
The Cyber Essentials framework is specific to the UK. It incorporates the very basic guidelines for keeping an organization’s IT infrastructure secure and protected against common cyberattacks. This framework was created in 2014 by the National Cyber Security Center (NCSC).
Cyber Essentials offers a self-assessment checklist, which an organization can follow and self-check if they meet the requirement standards as per the Cyber Essentials framework. On the other hand, an organization can opt for the “Cyber Essentials Plus,” which is a certification granted by external auditors.
That said, this framework is designed around the following 5 controls that protect against the most common cyber attacks:
- Firewalls and routers
- Secure configuration
- Access control
- Malware protection
- Patch management/software updates
Federal Information Security Management Act (FISMA)
The FISMA framework falls directly under the Department of Homeland Security (DHS). Formed in 2014, it is a comprehensive cybersecurity framework designed to be implemented across all of America’s federal government information and systems.
The core guidelines of the FISMA framework align with the NIST CSF (discussed above). It is designed to protect valuable government information from cyberattacks and threats. Since it is crafted for federal agencies, satisfying the framework’s control systems can be a hassle since it includes sophisticated practices, guidelines, and security controls.
The following are the core of the FISMA principles:
- Information system inventory: The federal organization must maintain an inventory of all the cybersecurity systems utilized within the company.
- Risk categorization: The assets to protect, which inflict maximum risk, must be categorized according to their priority so they can be protected accordingly.
- System security plan: The organization must devise and maintain a security plan. It should cover things like the implemented security controls, security policies, a timetable for the introduction of further controls, etc.
- Security controls: Unlike other frameworks, FISMA does not encourage an organization to implement all security controls. Instead, it only guides to implementation of the controls relevant to the organization’s domain and functionality. Once the appropriate controls are selected and the security requirements have been satisfied, the organizations must document the selected controls in their system security plan.
- Risk assessment: The FISMA framework follows the NIST CSF guidelines when conducting a risk assessment. Risk assessments ought to be three-tiered to identify security risks at the organizational level, the business process level, and the information system level.
- Certification and accreditation: This framework is certification-based, which means that other authorized federal agencies perform annual audits to confirm that the organization meets the minimum standards.
Ignoring cybersecurity frameworks
If you are an organization dealing in IT or handling sensitive information and choose not to adhere to any frameworks, what’s the worst that could happen?
A LOT! Frameworks are designed to jump-start your cybersecurity infrastructure so you know what checks to perform, how to minimize the attack surface, how to handle incidents, how to generate reports, how to learn from those reports, and how to recover from an attack. If you do not follow frameworks, you are likely prone to cyberattacks, digital theft, data breaches, and much worst.
Additionally, if you are a registered organization, then you could face some serious financial penalties for not having implemented the basic security precautions.
Top cybersecurity frameworks: A summary
As mentioned earlier, there are different kinds of frameworks that focus on different aspects of cybersecurity within an organization. The table below summarizes the popular cybersecurity frameworks and what each of them provides guidance on.
| Cybersecurity Framework | Description |
| NIST CSF | Used by new and existing organizations. Designed to protect networks and assets from cyber threats. Includes the following principles: Identify, protect, detect, respond, recover |
| ISO/IEC 27001 & 27002 | Used by organizations that handle consumer data using Information Security Management Systems (ISMS). Audit-based certification. Guides how to approach risk assessment, control selection, and policy/rule implementation. It tells the requirements for establishing an ISMS. |
| CIS Control Framework | Used to protect a network from cyberattacks through access control and management, asset management, incident reports and responses, etc. It includes basic controls, foundational controls, and organizational controls. |
| SOC2 | Used within an organization handling client data, especially financial information. The framework is centered around security, availability, processing integrity, confidentiality, and privacy. |
| HITRUST CSF | Comprehensively protects healthcare patients’ data. Control systems are implemented through 14 categories, with 156 control specifications. |
| COBIT | An end-to-end guideline designed to help organizations manage their IT resources more effectively. Centered around the following 6 principles: Meet stakeholder requirements, holistic approach, dynamic governance, distinct governance from management, crafted to organization’s needs, and end-to-end governance. |
| Cyber Essentials | Framework for the UK. Basic guidelines for keeping an organization’s IT infrastructure protected against common cyberattacks. Suggests implementation of the following 5 controls: Firewalls and routers, secure configuration, access control, malware protection, and software updates. |
| FISMA | For federal agencies that are audited by other federal organizations. Adheres to the following principles: Information system inventory, risk categorization, system security plan, security controls, risk assessment, and certification and accreditation. |