Key Points
- In a Man in the Middle attack, the attacker secretly hijacks an active online session without alerting the browser or the web server and listens in and manipulates the data packet transactions.
Cyberattacks have been carried out since the beginning of the invention of the internet, and the same concepts are still being used to exploit the vulnerabilities that exist today. A Man in the Middle or MITM attack is one of those cyber attacks that have been around for a while, and we still find hackers using them today.
In a MITM attack, the hacker places themselves between an active real-time connection and eavesdrops on their conversation. If required, they may also be able to manipulate the exchange of information between the source and the destination devices.
This guide provides information on everything there is to know about Man in the Middle attacks, including the cautions you can take to avoid being a victim, and the immediate measures to perform in case you have already been targeted.
What is a Man in the Middle attack?
In a Man in the Middle attack, the attacker secretly becomes a proxy between a user and an application, or between two devices, and relays the information between them. The two original devices are unaware that their conversation has been hijacked and believe that they are communicating with the original device directly.
A MITM attack is a sort of session hijacking attack, where the perpetrator hijacks the original message stream, and listens in on the data packets, all without alerting either the source or the destination devices.
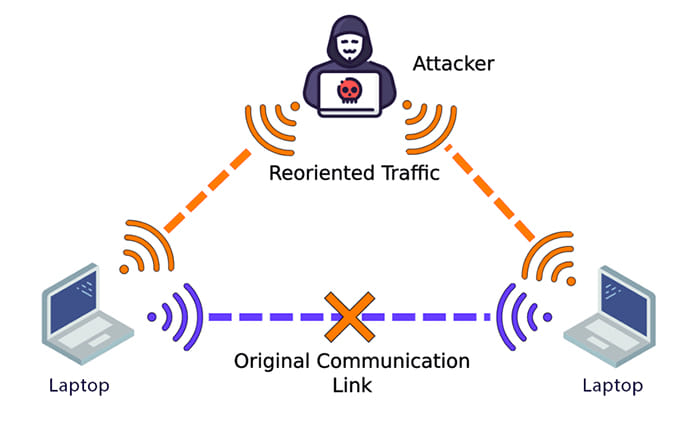
In the example image above, you can see that the original communication between the two laptops has been intercepted, and the communication is now transmitted through the attacker. The attacker now acts as a relay for the exchange of data between the devices.
How Man in the Middle attack works
An attacker needs to put themselves between the data exchange medium to listen in on the traffic. This can be achieved by injecting malware into the user’s device through emails, adware, or other malicious means.
An attacker cannot simply tap into a wire and listen in on the exchange of data packets between two devices. They first need to intercept the user traffic through a network before it reaches its destination using software tools, and if successfully done, they must then decrypt the information to make it human-readable.
There are several methods to achieve both of these phases.
Intercepting the communication
The first challenge for the attackers in a Man in the Middle attack is intercepting the communication between a device and the web. This can be done by several means, such as placing malware on the device, like spyware, that will send the data to the attacker. A more common method is setting up unprotected Wi-Fi hotspots.
Devices with a wireless network card will try to connect to the unprotected network thinking it is free internet, which is a compromised network. The attacker will then use a series of technologies to intercept the network traffic from your device to the internet (or any app), and back.
This interception attack can be performed using any of the following methods:
-
IP Spoofing

IP Spoofing In IP spoofing, the IP address in the packet headers is modified to make it look like the original sender of the data packet is some other source. An attacker can use this technique only to capture the data being sent inside the packets, or manipulate and change it before forwarding it to its original destination.
For example, when a user queries a URL, the attacker could respond to it with an acknowledgment packet with a modified header, pretending to be the original website. The user would then be communicating with the attacker, unknowing of the fact that it is an imposter and not the original URL that they wanted to access.
-
DNS Spoofing

DNS spoofing A Domain Name Server’s (DNS) purpose is to translate the string-based URL to an arbitrary IP address. A hacker can manipulate the entries in a DNS server to change the original IP address for a URL, and the victims would end up communicating with the attacker’s fake website, instead of the original one.
This method is often combined with a fake website that looks exactly like the original one, and the user has no idea that they are providing their credentials to the hacker.
-
ARP Spoofing

How ARP spoofing works. Source: Wikipedia ARP, or Address Resolution Protocol is used to map ever-changing IP addresses to a single MAC address. This way, regardless of a changing IP address, all traffic will be directed to the same destination.
ARP spoofing, also known as “ARP poisoning” is a technique used by attackers that maps their malicious MAC address with an IP address. This way, when a user queries a URL or an IP address, that information is sent to the attacker instead.
This interception method is adopted for Local Area Networks (LANs).
Using any of the methods above, a hacker can get on the same network as the victim and initiate unauthorized communication with their device. Once in, they now have to decrypt the exchange of data packets.
Decrypting the data
Normally, the communication by the user is encrypted using SSL certificates, which need to be decrypted, and only then is it useful for the attacker. The decryption process can also be carried out using various methods.
-
HTTPS Spoofing
The Hypertext Transfer Protocol (HTTP) is a protocol that communicates data between a browser and a web server. The data transfer data is usually protected with a digital certificate, known as an SSL certificate, which makes the simple HTTP communication into HTTPS.
In HTTPS Spoofing, hackers usually mimic a legitimate website to look exactly like it and also embed a fake, green padlock next to the URL bar/omnibox to make it seem like the website is secure with an SSL certificate, when in fact, it is not.
-
SSL Hijacking
Attackers can generate, or forge fake SSL certificates to authenticate on behalf of legitimate websites with the users when requested a TCP handshake. This process is known as SSL hijacking, and the attacker successfully establishes a connection with the victim, pretending to be a secure website.
-
SSL Stripping
As the name implies, in SSL stripping, the attacker “strips” the SSL certificate from a secure communication and downgrades the HTTPS protocol to just HTTP.
The attacker establishes a secure connection between the secure website and itself while maintaining a striped connection with the victim. This way, all communication with the user is bare and unsecured.
-
SSL BEAST
“SSL BEAST” stands for “SSL Browser Exploit Against SSL/TLS.” In this decryption method, an online application’s encrypted cookies are intercepted by malicious JavaScript on the victim’s PC planted by the attacker. Then the app’s Cipher Block Chaining (CBC) is compromised by decrypting its cookies and authentication tokens.
Tools used for Man in the Middle attacks
To be able to perform these attacks, an attacker needs a combination of services, tools, and skills. They need to perform packet sniffing, spoofing, stripping, and many other tasks to be able to successfully perform a Man in the Middle attack.
Various tools provide different functionalities. Here is a list of the most common hacking tools used in Man in the Middle attacks:
Note: This list is only for educational and research purposes.
- PacketCreator
- Ettercap
- Dsniff
- Cain and Abel
- Paros Proxy
- Burp Proxy
- ProxyFuzz
- Odysseus Proxy
- Fiddler (by Microsoft)
- mitmproxy
- Hetty
- BetterCap
- Proxy.py
Victims and purpose of Man in the Middle attacks
Man in the Middle attacks can be targeted at individuals as well as complete organizations. It depends on the intent of the attacker. A MITM attack can be carried out simply to listen in on the information, capture it, and sell it to the highest bidder. At other times, a MITM attack is carried out to manipulate and change the information communicated between the source and the destination devices.
As history tells us, most of the Man in the Middle attacks have been carried out against financial institutions, where information on millions of users has been compromised. Here are a few examples from our past:
-
DigiNotar
DigiNotar used to be a Dutch issuer of digital security licenses. In 2011, its data was compromised and the attackers gained access to 500 certificates for prominent websites, including Skype and Google.
The attackers manipulated the end users by mimicking legitimate websites where they entered their very real credentials. With this information, DigiNotar took a dramatic strike and had to file for bankruptcy due to the losses.
-
Superfish
Superfish Visual Search was an adware that came preinstalled with some Lenovo computers in 2015. This software would insert advertisements into the user’s encrypted traffic, making it insecure. The makers of Superfish obtained user information with this technique. However, Microsoft patched this vulnerability through a Windows Defender update in February 2015.
Since then, Superfish has been notorious, resulting in complete disablement.
-
Equifax
Equifax is a credit reporting agency, which means that it hoards sensitive data on individuals. In 2017, that data was breached and nearly 150 million individuals were compromised.
This great heist was performed through a Man in the Middle attack since they failed to patch a vulnerability in their own applications. Furthermore, sometimes, the application wasn’t even using a secure HTTPS connection to communicate with the server.
Other than these examples, you will find a lot of different examples of Man in the Middle attacks in the past. There have been many that compromised the financial information of individuals who then became victims of unauthorized purchases and transactions.
This highlights the severity of MITM attacks, and that they should be taken seriously, regardless of the nature of your work.
How to detect Man in the Middle attacks
It can be difficult to detect Man in the Middle attacks since the attackers hijack an active session. However, monitoring certain parameters and observing network traffic can pinpoint an ongoing MITM attack, or intimate the sysadmins when a MITM attack was performed.
One way to detect a MITM attack is to keep an eye out for repeated disruption of services. The attackers need to disconnect a user session before hijacking it, leading to the disruption of services. If you observe this happening frequently and unexpectedly, you may be under a Man in the Middle attack.
An observation that the network admins can make is the frequent requests to websites that are similar to the legitimate ones. For example, instead of sending requests to “www.itechtics.com”, the user could be communicating with “www.techtics.com”. This would mean that the victim is unaware of the fact that they have established a connection with a counterfeit website.
Apart from these observations, a technical parameter that would inform the administrators of a Man in the Middle attack is performing a real-time latency examination. Latency is the time it takes for the data packets from point A to reach point B. If certain data packets are taking longer than the rest, this would indicate a potential MITM attack, since it takes a few extra milliseconds for the attacker to manipulate the data packets between the two endpoints. This latency comparison can be done using the timestamps in the packet headers.
Deep Packet Inspection (DPI) and Deep Flow Inspection (DFI) can also be used in network monitoring to identify MITM attacks. Network monitoring tools can access data like packet size and length with such tools, which can be used to detect unusual network activity.
Another efficient method of detecting a Man in the Middle attack is by using Intrusion Detection and Prevention Systems (IDPS). Anomaly-based IDS can spot and highlight packets where the traffic is unusual from the rest, and inform the administrators.
Finding unusual traffic and latency problems is only the first step in detecting a man-in-the-middle attack. Further forensic analysis of the malicious traffic will be required to confirm whether it was a Man in the Middle attack, or something else. If it is confirmed that the attack was, in fact, a MITM attack, then further investigation will be required to trace it back to the source/victim of the attack.
The IP address, DNS name, and the server’s X.509 certificate data, which contains an identity and a public key, are crucial parameters needed for forensic investigation. In the event of an incident, this information also makes compliance audits simpler.
Although complex, these are the effective methods of detecting MITM attacks, since these attacks can barely be detected simply based on the visible symptoms.
How to prevent Man in the Middle attacks
Since detecting Man in the Middle attacks is a hassle, it is best to prevent such attacks. You can adopt best practices and mitigation methods to prevent yourself from falling prey to MITM attacks. Here are a few considerations that you should always keep in the back of your mind to prevent MITM attacks:
-
Avoid connecting to unsecured and public networks
Public Wi-Fi networks, which are usually left unprotected, are the main intrusion points for attackers. When the victim and the attacker are on the same network, it becomes easier for them to intercept the communication. they can then implement IP or ARP spoofing to mimic a legitimate website, grabbing onto your provided information.
-
Only access secure websites
Another basic instinct when on the internet is to access only the secure websites that have an HTTPS connection. Check that the URL includes “HTTPS,” and not just “HTTP.” The HTTPS will also be accompanied by a padlock sign, indicating that the website is secure.
Most modern browsers automatically intimate the users when they are about to access an unsecured website. This should be the queue to move away from it.
-
Beware of phishing emails
Phishing is when an attacker tries to obtain your credentials through fraudulent emails and other social engineering techniques. For example, they might send you an email impersonating a bank or a website and asking you to click on a website link, that looks very much like the original website, and enter your sensitive information.
Other phishing techniques include sending a malicious link that will download malware from the internet, or redirect the victim to a malicious URL.
Therefore, it is advised to be cautious of phishing emails, as well as ads, and do not open any links from sources that you do not know or trust.
-
Use Virtual Private Networks (VPNs)
A VPN encapsulates the online session and the data communication is encrypted. An attacker would only be able to decrypt this data if they have the correct decryption key, even if they successfully intercept the communication.
In the case of organizations, the IT administrators should ensure that anyone connecting from outside the company’s network logs in using a VPN, or otherwise won’t be allowed to remotely access any servers, ensuring that all communication outside the network is going through VPNs.
-
Use endpoint antimalware
Normally, Man in the Middle attacks are triggered through malware, and by human action. Therefore, it is paramount that you use endpoint security software and keep the individual devices protected from malicious files and links.
Additionally, it is advised to perform frequency scans and quarantine any malicious files, if found.
-
Log out of financial/sensitive websites/applications
Leaving your account logged in to sensitive apps and websites is like an invitation for hackers to come in and steal what they want. Therefore, make a habit of logging out of all apps and websites that contain sensitive information, like your finances.
Additionally, avoid saving passwords in the browser’s password manager, since those are not secure.
This concludes the conventional methods you can adopt to reduce the risk of falling prey to Man in the Middle attacks. Ensuring that the attackers do not gain access to the same network as you is step one, step two is making sure that they cannot intercept the data packets. Even if they succeed with that, ensuring that they cannot decrypt the data is step 3 in the prevention process.
How to recover from Man in the Middle attacks
If you believe that you have been targeted by a Man in the Middle attack and your information has been compromised, you need to take certain measures to stop the attack then and there and prevent further information from ending up in the hacker’s possession.
Here are a few things you must do to recover after a Man in the Middle attack, in the given order:
-
Take the network offline
The first line of defense, in most sorts of cyberattacks, is taking the entire network offline, especially in the case of organizations. If your home device has been compromised, I would suggest disconnecting the WAN cable coming into the router.
-
Run a deep scan
The next thing to do is run a deep malware scan on all of the devices, including mobile phones, computers, and tablets. this can be done using the native antivirus, or third-party antivirus software.
-
Disable automatic proxy server detection
The Web Proxy Auto-Discovery (WPAD) can be leveraged to conduct MITM attacks, which will allow unauthorized proxy servers to relay traffic between a source and a destination. This can be prevented by disabling the automatic proxy server detection on your devices.
On Windows, you can disable it by going to Settings > Network & internet > proxy, and toggle the slider in front of “Automatically detect settings” into the Off position.

Disable auto-detection of proxy settings in Windows -
Change all passwords
As a precautionary measure, you should change all of your computer and web passwords to make sure that the attacker does not already have them. Of course, to change your web passwords, you must go online. For that, I recommend using a different network for the time being, than the one that was compromised.
-
Tighten digital security
In the end, you should focus your resources toward tightening the digital security. You can employ advanced firewalls, like Next-Gen Firewalls (NGFW), or invest in a professional security team that will perform detailed forensics on how the attack occurred in the first place, and take the necessary actions to patch up the vulnerabilities.
This concludes the methods to recover yourself after a Man in the Middle attack. As you may observe, there isn’t much you can do after your sessions have been compromised. Therefore, prevention is the best method to keep yourself secure from online threats, including MITM attacks.





